Why Do I Need a Web Application Firewall?
Three layers of an IT system: application, system, network
All corporate IT systems consist of three layers – application, system, and network. Applications are software programs run on computers and hosted by servers. Systems refer to hardware devices such as computers, servers, and other business machines. A network is a connected web of these hardware devices, allowing information to be transmitted from one to another.
The simple act of a person using a website involves all three layers of the IT system. How? When a client (i.e. user) from outside the local area network (LAN) logs in to a web application hosted by a local server, they are in fact sending a request to the local server to retrieve their account-related data from the database and bring the information forward to the web application interface. In this process, the client is essentially communicating with the system (i.e. server) in the network (i.e. LAN) using the application (i.e. website) as a medium.
Securing an IT system
External traffic can gain access to a system through two different paths. It can either enter directly through the network, or enter indirectly through a web application as described above. Normally, when the network access protocols and web applications are configured properly, they are not supposed to grant access to unauthorized users. However, attackers could always exploit vulnerabilities and flaws in them to gain access to the systems. This is why we have firewalls to protect them.
Network firewall vs. web application firewall (WAF)
Just as how there are two paths to enter a network, there are two different types of firewalls used to secure each path.
The word “firewall” is mostly used to refer to a network firewall. A network firewall protects a secure LAN network from a less secured or unsecured network. It is placed on the perimeter of the LAN network, acting as a barrier and controlling access to the LAN network by blocking illegitimate HTTP and HTTPS traffic from entering. Run on a dedicated hardware appliance, a network firewall watches the network layer by blocking unauthorized access from less secure zones (see figure 1).
Different from a network firewall, a web application firewall (WAF) filters traffic that enters through the application layer. It is usually placed close to the internet-facing applications. It is extremely adaptable in which it can be run on a dedicated hardware appliance, through a virtual machine, or deployed as SaaS in the cloud (see figure 1).
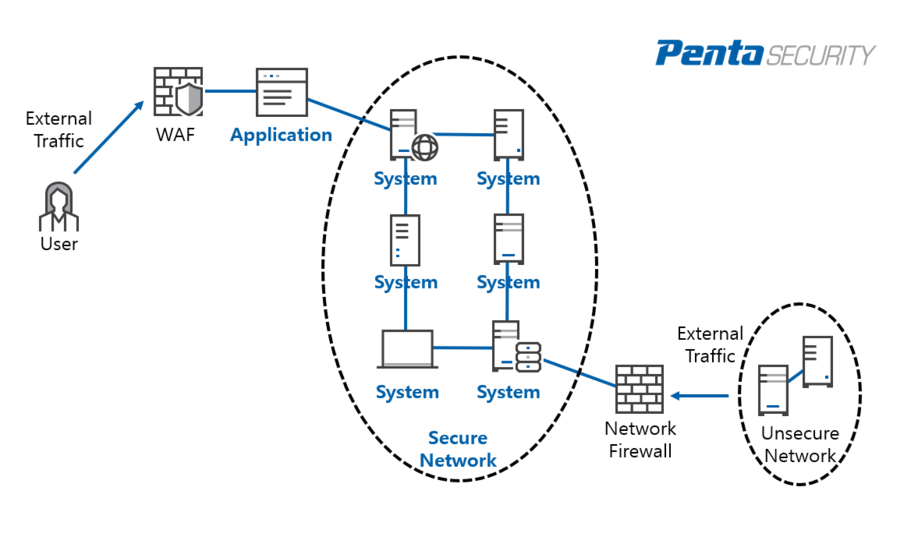
<Figure 1. Three Layers of IT System, Network Firewall vs. WAF>
Why do I need a WAF?
Websites have become the primary channel for most businesses to exchange information with customers and stakeholders. Most websites contain applications in them. For example, every web form is an application – after inputting the login credential, the application server would retrieve the user’s data from the database to the front end.
As explained earlier, a network firewall stops malicious packets from entering into the systems through direct network connections. However, it is incapable of stopping intrusions from the application layer, which already sits within the network. Having a network firewall alone without a WAF is like having your door locked while leaving the windows open.
Why is it important to secure the application layer? According to research by Penta Security, over 70% of hacking attempts are carried out through the web. Among them, over 90% are targeted at web applications, meaning that well over half of all cyberattacks are directed at web applications.
Reducing the Risk of Data Breaches
Without properly securing web applications, organizations face a very high risk of leaking their data. Attackers can always exploit the vulnerabilities of an application to gain access to the database, after which they could view, change, delete, and even exfiltrate data. Data breaches are one of the biggest threats for a business, potentially leading to the deterioration of customer trust, reputation, brand value, share value, as well as direct financial loss due to heavy fines.
CCPA, GDPR, PCI-DSS, and HIPAA Compliance
In most cases that involve personal data of customers and third parties, organizations are legally required to have proper security measures in place. A WAF is one of the most essential components in meeting compliance, apart from data encryption and multi-factor authentication.
WAPPLES, a WAF customizable to all needs
For those looking for a WAF to protect your business, we recommend putting WAPPLES on your shortlist. Developed by South Korea’s largest information security provider, it is a great alternative to its big two American counterparts.
With the biggest market share in Asia Pacific, WAPPLES has contributed to countless cases of customer success, effectively preventing data leakage and keeping compliant to regulations.
Watch this exciting video to learn more about WAPPLES’ amazing features and benefits.
To learn more about WAPPLES, click here.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D’Amo
Identity and Access Management: ISign+
Automotive and Mobility Security: AutoCrypt
