WAPPLES
Intelligent Web Application and API Protection
WAPPLES is a Web Application and API Protection solution(WAAP) that utilizes logical analysis to protect web applications, APIs, and mobile apps from cyber attacks.
As a market share leader in Asia-Pacific, WAPPLES is an effective solution against sensitive data exposure, website defacement, API schema protection, malicious bots, and DoS, helping organizations exceed regulatory compliance.
Powered by a logical COCEP™ engine, WAPPLES reponds newest threats, including attacks in Advanced Persistent Threats (APT) launched by malicious groups to thieve data assets of governmental organizations or enterprises. The Lower false-positive rate, based on the intelligent logical COCEP™ detection engine, of Penta Security’s WAAP solutions including Cloud based one is recognized by Gartner in 2023 market guide.

Intelligence Allows Top Performance
While traditional WAFs depend on high-maintenance signature updates for low-accuracy pattern-matching, WAPPLES uses a logic-based detection engine called COCEP™ (Contents Classification and Evaluation Processing).
Utilizing 39 pre-configured detection rules, modified and even unknown attacks are categorized and blocked heuristically and semantically. This proprietary technology allows WAPPLES to deliver superior security with industry-leading accuracy and low false positive rates under various network environments.
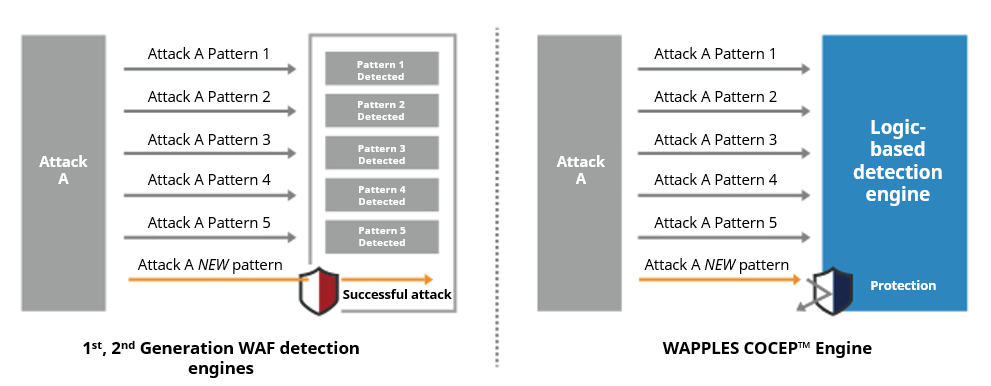
Through the analysis of an attack’s characteristics, WAPPLES is able to identify attacks that utilize new patterns of exploit that often bypass typical WAFs utilizing signature-based detection engines.
1st and 2nd generation WAFs that operate on blacklists and whitelists lag behind due to their reliance on signature updates to detect the latest threats. In comparison, the sophistication of security that WAPPLES can provide greatly surpasses that of signature-based WAFs.
WAPPLES Product Family and Related Services
Features
Appliance-type WAAP Solution
· Logic-analysis based COCEP™ engine protects websites against various cyber threats including OWASP Top 10 and API Security Risks
· Extremely low false-positive rates through heuristic and semantic traffic analysis
· Utilizes 39 detection rules that can be fine-tuned to create robust custom security policies
· Defense from known, zero-day, and HTTP DoS attacks
· Validity testing (Luhn: ISO/IEC7812) prevents leakage of sensitive data
Easy to Install & Configure
· Minimal changes to existing systems
· Quick setup with pre-configured security policies
· Statistics visualized on a centralized dashboard
· Intuitive and easy-to-use GUI management console
· Increases efficiency in web security management
Supports Various Environments
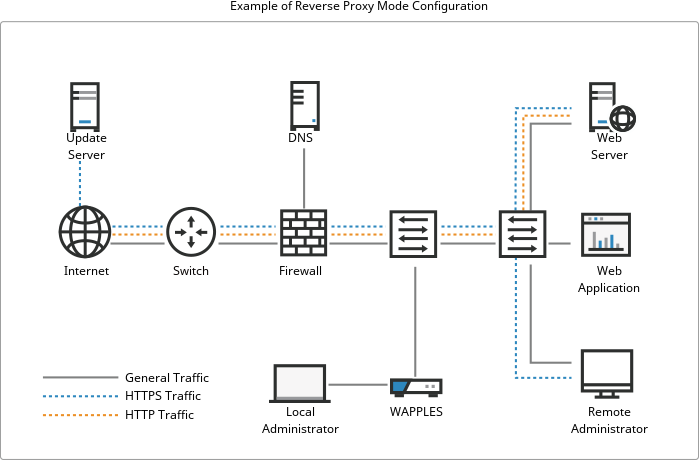
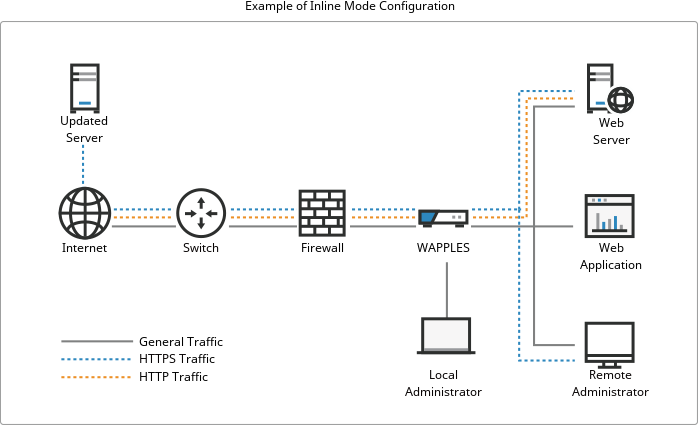
· Can be deployed in Reverse proxy, Inline, or High Availability (HA) configuration modes
· Support for EtherChannel and Multi-Segment
· Integration with SIEM
High Performance and Stability
· Optimized core provides enhanced performance
· High processing power with in-memory computing capability
· Stable performance even with strict security policy settings enabled
· Increased bandwidth through bonding technology
Deployment
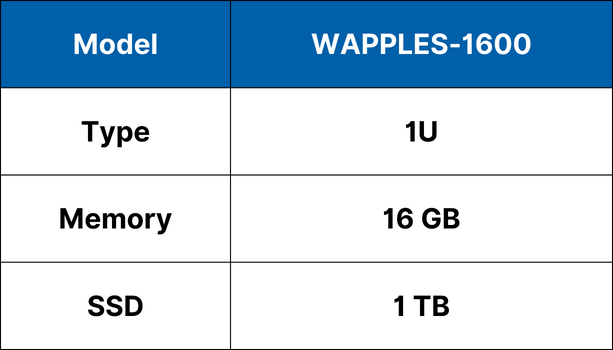
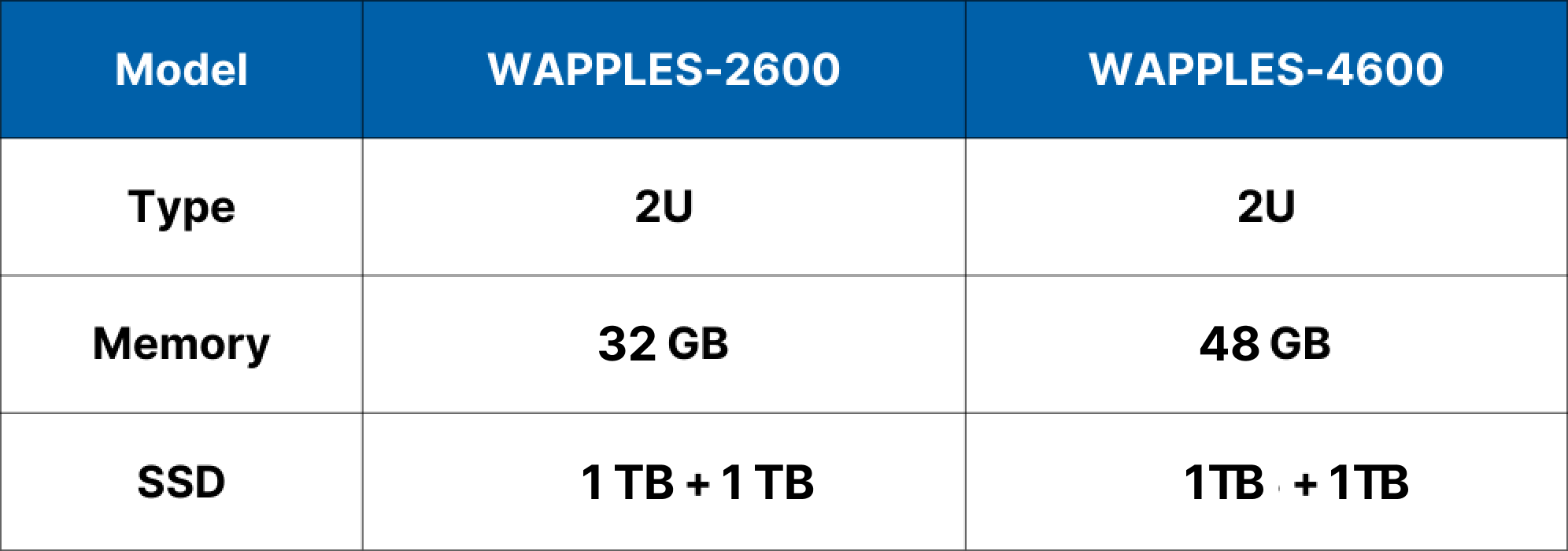
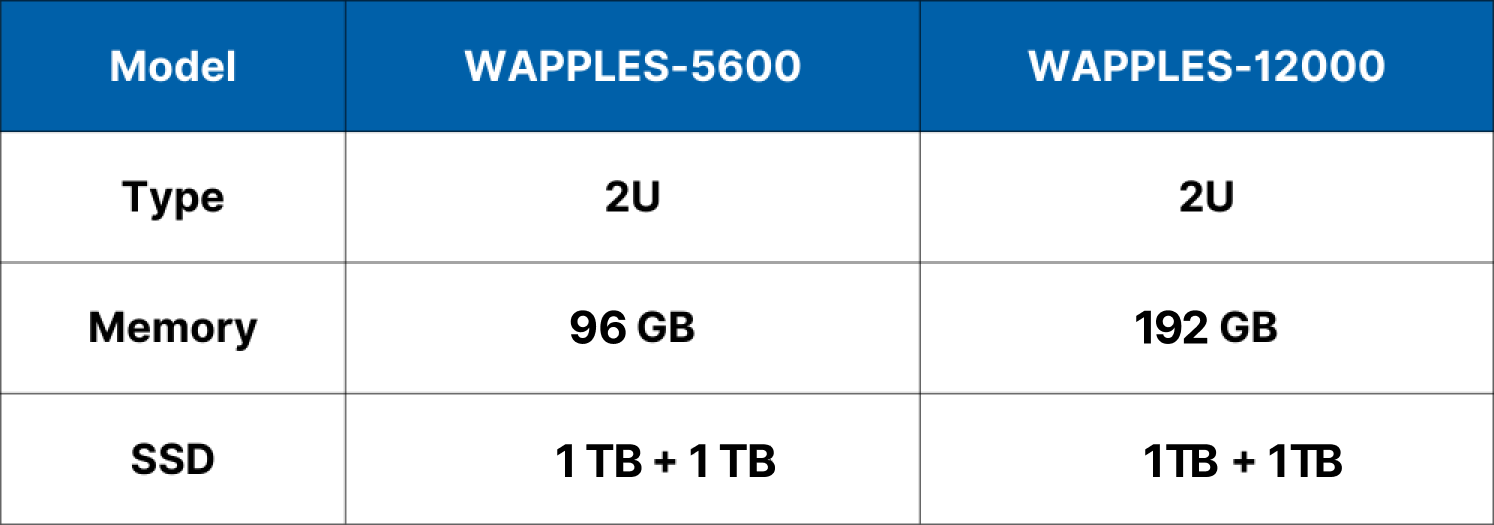
Specifications
Economy
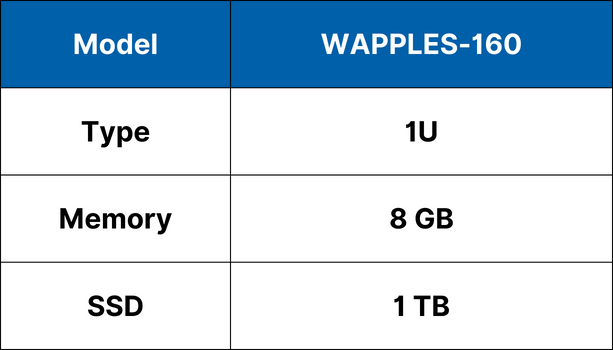
Value
Performance
High-End
*Specifications subject to change without notice.
Implementation
When a customer chooses to deploy WAPPLES, a thorough analysis of the customer environment will be conducted prior to installation. This is important for optimizing policy settings tailored to specific operational and business needs to achieve an optimal configuration. Post-installation, detection logs are also monitored over a period of time and analyzed to further fine-tune the security policies and complete the implementation process.
- Pre-Inspection
- Pre-inspection
- Install and Configuration
- WAPPLES installation
- WAPPLES configuration
- Operation testing and demonstration
- Supplement Policy
- Detection log analysis
- Analysis report
- Policy modification