Smart Factory Security
Secure IoT for Cyber Physical Manufacturing
After the announcement of “Industry 4.0,” ‘Smart Factories’ have emerged as an important topic in the IoT era. To develop a Smart Factory, tens of thousands of sensors are required and it is necessary to track down the location of parts in real time while collecting and analyzing data before proceeding to the automation process.
Complex and precise industrial management systems remain vulnerable to malicious attacks by hackers. Malfunctions of certain facility parts can compromise safety and quality of products. They can even lead to severe personal injuries and property damage. To solve this problem, an organization was established to respond to Smart Factory security threats. In 2008 in the U.S. and Korea, the Smart Factory Group was organized to deal with security issues.
At Penta Security, we have extensive security system references and expertise in Smart Factory security such as AMI (Advanced Metering Infrastructure). Companies looking to introduce Smart Factories are required to authenticate and protect communication between their systems while ensuring the security of their servers and infrastructure in order to prevent personal injuries and maintain processing quality.
Case 1 Sewing Machine Monitoring Solution
Sewing companies can deploy an IoT monitoring solution for sewing machines, with networked sewing machines sending data to a centralized cloud server. This can mean significant savings to the operator, since the manufacturing times of the machines can be controlled much closely and from a remote location. However, this also allows for remote attacks which can wipe out any savings (and more) in a matter of seconds.
A sewing company came to us for security in their factory. Penta Security advised that, for starters, security was needed for communication between the network of sewing machines and the monitoring server.
- Provide device authentication for each industrial sewing machine
- Encrypted communications of data between sewing machines and cloud server, as well as with each other
- Ensure data integrity of information being sent to monitoring server
Case 2 Smart Factory Monitoring Service
A smart factory monitoring service provider contacted us for security for their factory administrator clients. This partner was looking to offer app-based monitoring solution for factory equipment. This would allow this partner to provide their smart factory monitoring services. But an attack was a risk they could not ignore before providing these services, since security is required for communications between equipment, and with monitoring servers, and of course, the devices (phones & tablet) communicating with that server.
About FactoCrypt
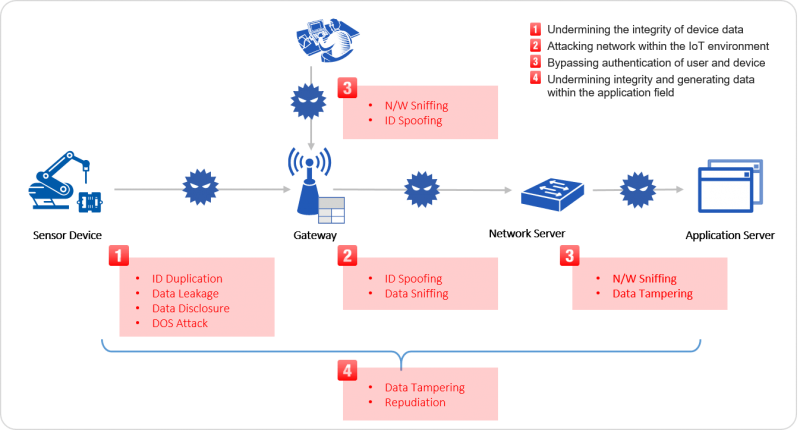
There are four types of security threats that need to be dealt with in the IoT-based Smart Factory environment. Hackers attempt to compromise the integrity of data and attack networks in the IoT communication environment through N/W sniffing, or data tampering repudiation. Therefore, all these threats need to be dealt with in order to ensure security in Smart Factories.
FactoCrypt Structure
FactoCrypt is designed to protect the Smart Factory environment against the four main types of security threats. By installing H/W-based security modules and creating a secure IoT network environment, it can maintain the integrity of data while protecting networks in the IoT communication environment. In addition, the solution introduces PKI (Public Key Infrastructure) technology to provide certificates for each device and user in order to prevent N/W sniffing. Finally, a customized security environment is created based on the experience and know-how we have gained while working with corporate clients in order to prevent data tampering in the application areas and maintain the integrity of data.
Want to learn more?
IoT brings a whole new world of possibilities. While smart factories can mean drastic savings in operational expenses and remote monitoring, IoT future does come at a price. Like all IoT applications, security needs to be assessed and implemented before any connections are made, in order to make all the convenience not simply possible – but secure.