Web Application Firewall (WAF)
A web application firewall protects your web applications
What Is a Web Application Firewall?
A web application firewall (WAF) is different from your typical network firewall (firewall). It is a solution developed specifically to address an often neglected but critical component of the security architecture — application layer security.
Why Is a Web Application Firewall Necessary?
Modern enterprises deploy a diverse array of web applications. Whether it’s public-facing websites or private intranets used for cross-team collaborations, the inspection of web traffic for threats needs to be granular and also intelligent enough to adapt to new and custom web apps.
The network firewall, which filters network traffic instead, is severely limited in protecting web assets. Because a network firewall’s access control is based on network-layer attributes, it is incapable of stopping attacks from applications already authorized to communicate through the firewall.
On the other hand, a web application firewall inspects data packets on the application level, validating inputs and detecting abnormalities in web protocols to identify application-specific threats.
Just as its name suggests, the basic function of a WAF is to detect and block web attacks like SQL Injection and Cross-Site Scripting (XSS) attacks. By blocking web attacks, web application firewalls serve as an effective solution against sensitive data leakage, unauthorized access and website defacement or cross-site request forgery (CSRF).
Evolution of Web Application Firewalls
Generations of WAF technology can be distinguished based on their main operating principles.
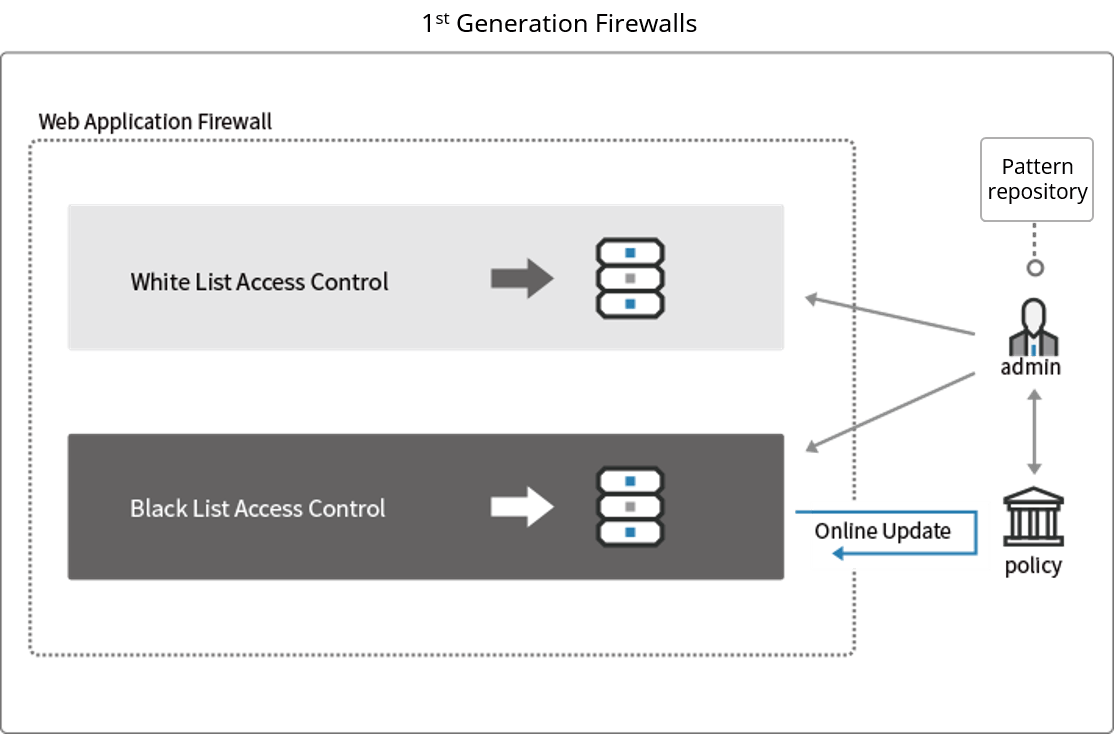
1st Generation WAF: Pattern-matching detection
The first generation of web application firewalls utilized two types of lists to determine whether or not to block traffic: whitelists and blacklists.
The whitelist is a list of characteristics that define legitimate traffic and the blacklist is a list of dangerous attack patterns. However, 1st Generation WAFs oftentimes mistakenly identify a safe access as an attack and block safe traffic. This is called a “false positive”. To reduce these misdetections, an administrator had to update both blacklists and whitelists constantly.
Not only did 1st Generation WAFs place a significant burden on system administrators, they were not particularly effective.
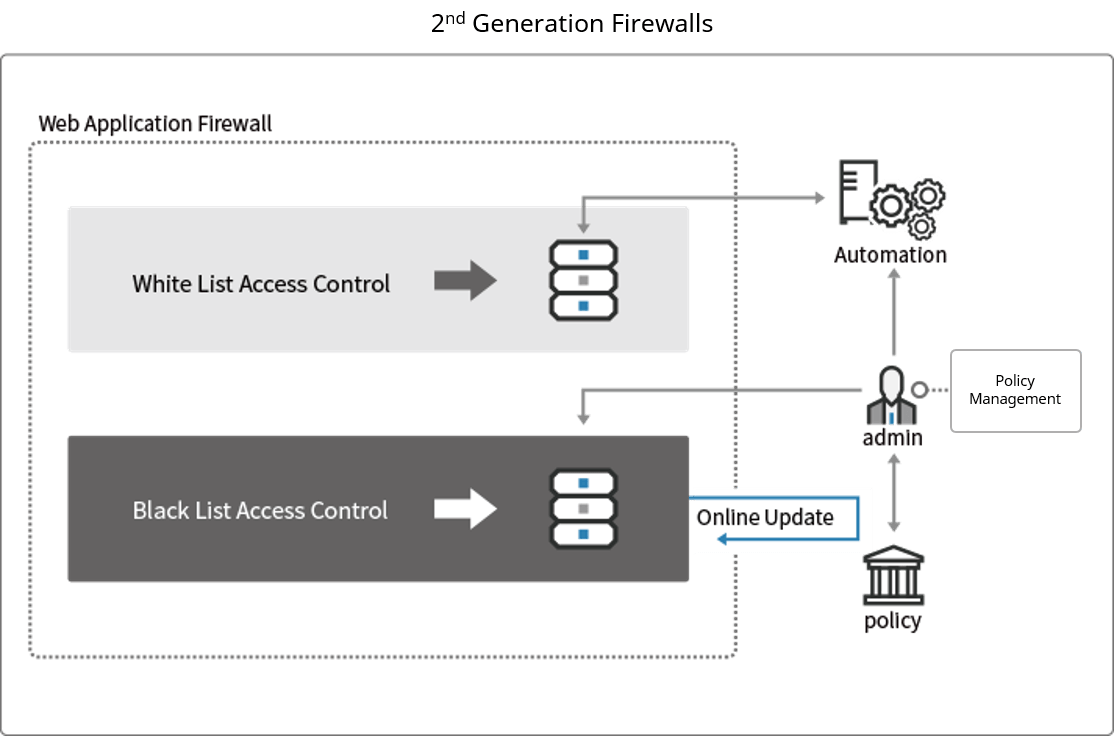
2nd Generation WAF: Automated whitelists
The second generation of web application firewalls automatically established whitelists by monitoring web applications over a period of several weeks.
However, this approach is not suitable in the current web environment where web attack patterns are rapidly changing. In addition, the whitelists that are generated still required manual configuration by an administrator who also has to constantly maintain blacklists of all conceivable attacks.
As such, the 2nd Generation WAF failed to significantly alleviate the burden on system administrators. To address all these issues, a third generation of WAFs was developed — the “Intelligent WAF”.
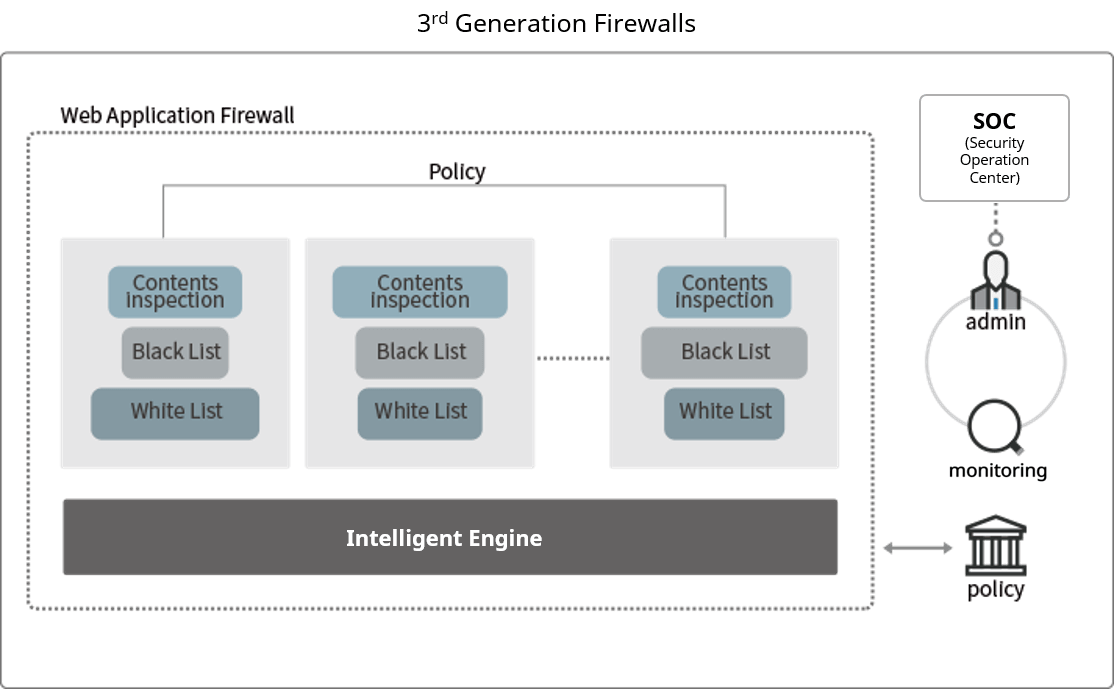
3rd Generation WAF: Logic-based detection
The third generation of web application firewalls combine various techniques such as blacklisting, whitelisting and data packet analysis to logically detect and categorize attacks.
In this way, false positives encountered are greatly reduced compared to with 1st and 2nd Generation WAFs. Furthermore, due to the logic-based approach to detection, new variants of attacks, along with modified attack patterns can be detected by intelligent 3rd Generation WAFs with minimal signature updates. Essentially a signature-free solution, the performance degradation impact of previous generations of signature-based WAFs relying on continuous signature updates is now avoided.
System administrators can instead focus more on policy management, optimized around attack characteristics, rather list management which is inefficient.
WAPPLES – The Intelligent Web Application Firewall
WAPPLES is one of these 3rd Generation WAFs which, utilizing signature-free detection mechanisms, require low operational workload for installation and maintenance.
The COCEP™ (Contents Classification and Evaluation Processing) engine detects web attacks by logical analysis, and the difference can be seen in the example below.
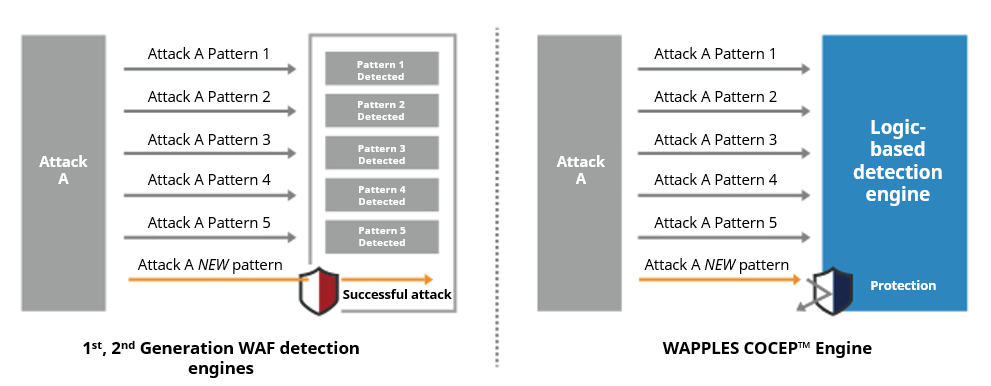
In the above illustration, Attack Pattern A, when modified, is blocked by WAPPLES but not by 1st or 2nd Generation WAFs.
Take for example, an attack with the pattern [A is (name of fruit)]. If only [A is apple], [A is banana] and [A is orange] are included within the list of detection signatures, a new attack like [A is strawberry] will pass through undetected.
On the other hand, if [A is] is added to the list of detection signatures, in order to block modified attacks like [A is strawberry], non-attack variations like [A is (color)] will all be misidentified as malicious accesses, resulting in a great number of false positives.
WAPPLES’s COCEP™ engine, which doesn’t solely depend on simplistic signature or pattern matches, can analyze whether what follows after [A is] indeed has the characteristics of an attack. Through heuristic and semantic analysis of attack techniques, Penta Security’s WAPPLES can block modified and even “unknown” attacks.
In this way, WAPPLES achieves superior detection accuracy while reducing false positives.