We are proud to announce that Penta Security has been named 2025 South Korea Company […]
Read moreAll posts tagged: waf
[Penta News] WAPPLES Wins 2025 National Service Awards for the Second Consecutive Year
Penta Security’s intelligent WAAP (Web Application and API Protection) solution, WAPPLES, has received the Cybersecurity […]
Read moreWhat Is Web Application and API Protection (WAAP)?
Web Application and API Protection (WAAP) is a term used to describe advanced web application […]
Read moreWhat Is a Reverse Proxy and What Does It Mean to Enterprise Security?
What Is a Proxy Server? At the most fundamental level of internet communication, whenever a […]
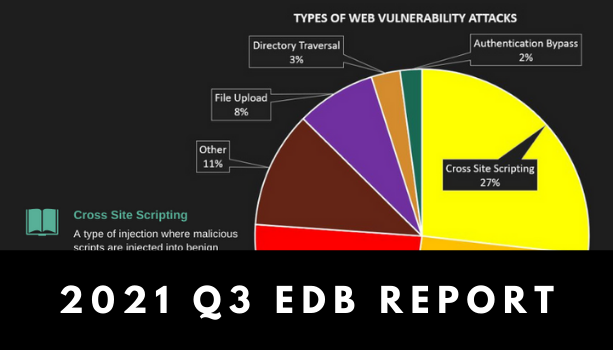
Read moreInfographic: Web Vulnerability Trends in Q3 2021
There was overall a slight decrease in the number of reported web vulnerabilities during the […]
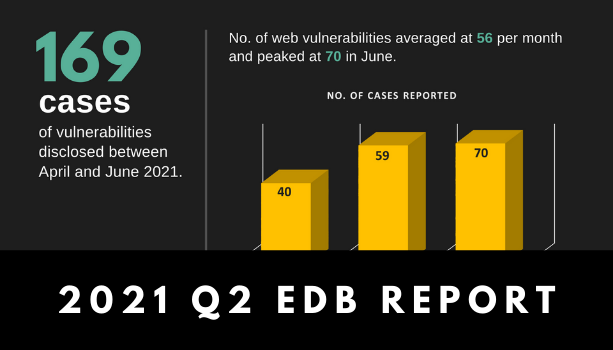
Read moreInfographic: Web Vulnerability Trends in Q2 2021
The number of reported web vulnerabilities increased throughout the second quarter, with a significantly higher […]
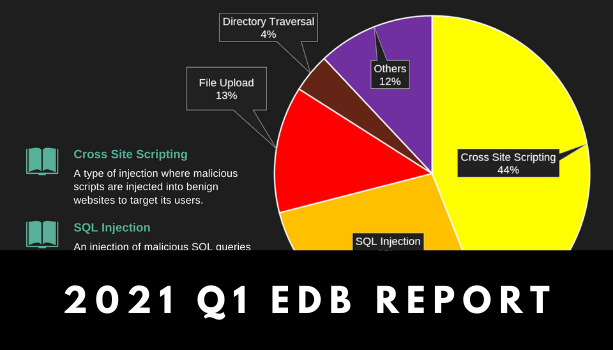
Read moreInfographic: Web Vulnerability Trends in Q1 2021
A significant number of web vulnerabilities were reported in January 2021. Among them, cross site […]
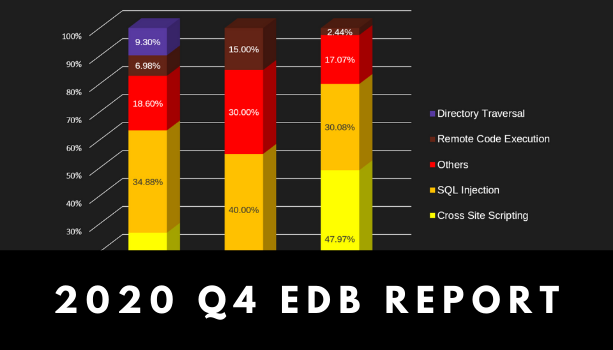
Read moreInfographic: Security Trends and Risks in the 4th Quarter of 2020
As 2020 came to an end, we saw a significant rise in the number of […]
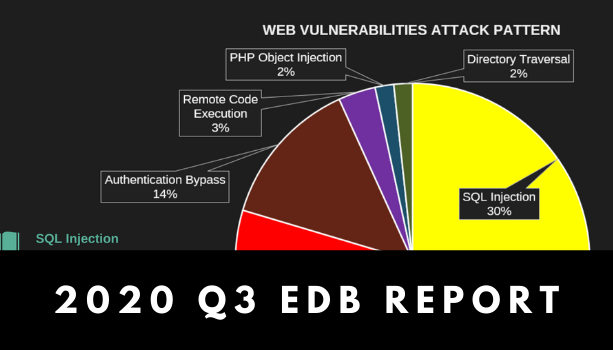
Read moreInfographic: Security Trends and Risks in the 3rd Quarter of 2020
Compared to previous quarters, we witnessed an overall decrease in the cases of vulnerabilities in […]
Read morePenta Security Enters Indonesian Market by Signing New Distributor PT. Prospera Aswindra Teknologi
Penta Security Systems Inc. signed a distribution agreement with PT. Prospera Aswindra Teknologi, Indonesia’s leading […]
Read more