Web Application and API Protection (WAAP) is a term used to describe advanced web application […]
Read moreAll posts tagged: web application firewall
Penta Security and PT. Prospera Aswindra Teknologi Highlight AI-based Web Application Firewall in Indonesia
JAKARTA, Indonesia, July 26, 2022 — Penta Security, an award-winning WAF provider from South Korea, hosted a […]
Read moreWhat Is a Reverse Proxy and What Does It Mean to Enterprise Security?
What Is a Proxy Server? At the most fundamental level of internet communication, whenever a […]
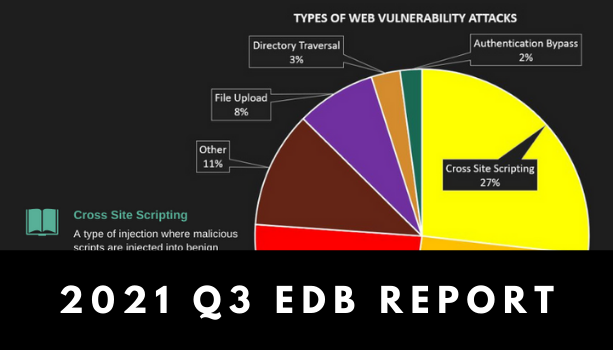
Read moreInfographic: Web Vulnerability Trends in Q3 2021
There was overall a slight decrease in the number of reported web vulnerabilities during the […]
Read moreAll You Need to Know About the 2021 OWASP Top 10 Update
The 2021 OWASP Top 10 Cyberattacks on web applications have become more intense and sophisticated, […]
Read moreYour Cybersecurity Team, Explained
Most people have seen hackers or hacker groups portrayed in mainstream media, and have a […]
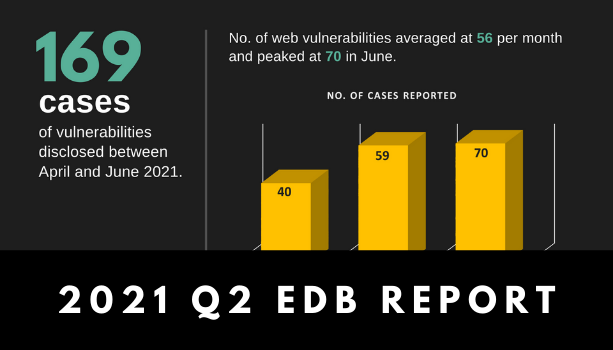
Read moreInfographic: Web Vulnerability Trends in Q2 2021
The number of reported web vulnerabilities increased throughout the second quarter, with a significantly higher […]
Read moreWhat Are APIs and How to Protect API Vulnerabilities?
What Is an Application Programming Interface (API)? Most people are familiar with the term “user […]
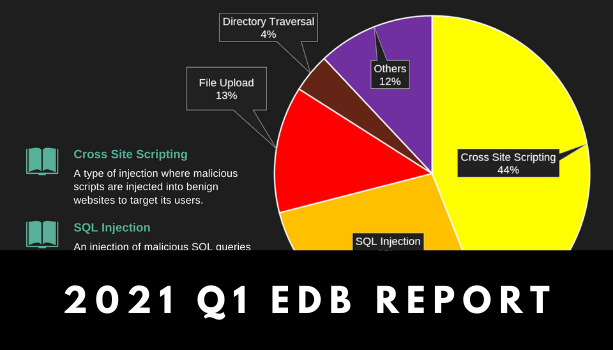
Read moreInfographic: Web Vulnerability Trends in Q1 2021
A significant number of web vulnerabilities were reported in January 2021. Among them, cross site […]
Read morePenta Security Named Most Innovative Web Application Security Provider During RSA Conference 2021
SAN FRANCISCO, United States, May 20, 2021 – Penta Security announced today that its web […]
Read more