All You Need to Know About the 2021 OWASP Top 10 Update
The 2021 OWASP Top 10
Cyberattacks on web applications have become more intense and sophisticated, making it essential for each organization to design a strategic defence and response plan based on the most common and dangerous web intrusion methods. To do so, web application developers and cybersecurity experts turn to the OWASP Top 10 to get a grasp of the most relevant security risks.
What is OWASP? For over 20 years, the Open Web Application Security Project (OWASP) Foundation has been doing intensive research on web application vulnerabilities and attack trends, establishing a set of industry guides and standards for software security. Among them, the OWASP Top 10 is the most popular and widely used awareness guide for web application security. The list outlines ten of the most critical web security risks that are relevant at the present time.
Compiled using research results from dozens of partner organizations, the OWASP Top 10 list was first published in 2003 and gets an update once every three to four years. In September 2021, the list received its first update since 2017, illustrating some of the latest threats to web security. In this article, we take a deep dive into the new update, starting with what has changed from four years ago.
What Has Changed Since 2017?
Rather than speaking of what has changed, perhaps it is more accurate to say what has been added. The 2021 OWASP Top 10 did not actually drop any item from the 2017 list. In fact, it broadened and combined some of the old items to clear up room to add a few more new threats that evolved recently.
Broadened Items. As seen in the diagram below, Sensitive Data Exposure was reframed as Cryptographic Failures to account for all types of data exposures, leaks, and breaches due to the lack of encryption or database misconfiguration.
Combined Items. Cross Site Scripting was combined into Injection since it has been considered a form of injection attack. Next, XML External Entities was combined into Security Misconfiguration because these attacks commonly exploit misconfigurations in XML specification. Lastly, Insecure Deserialization was combined with a new item named Software and Data Integrity Failures.
Added Items. Three items were added to the list. These are Insecure Design, Software and Data Integrity Failures, and Server-Side Request Forgery.
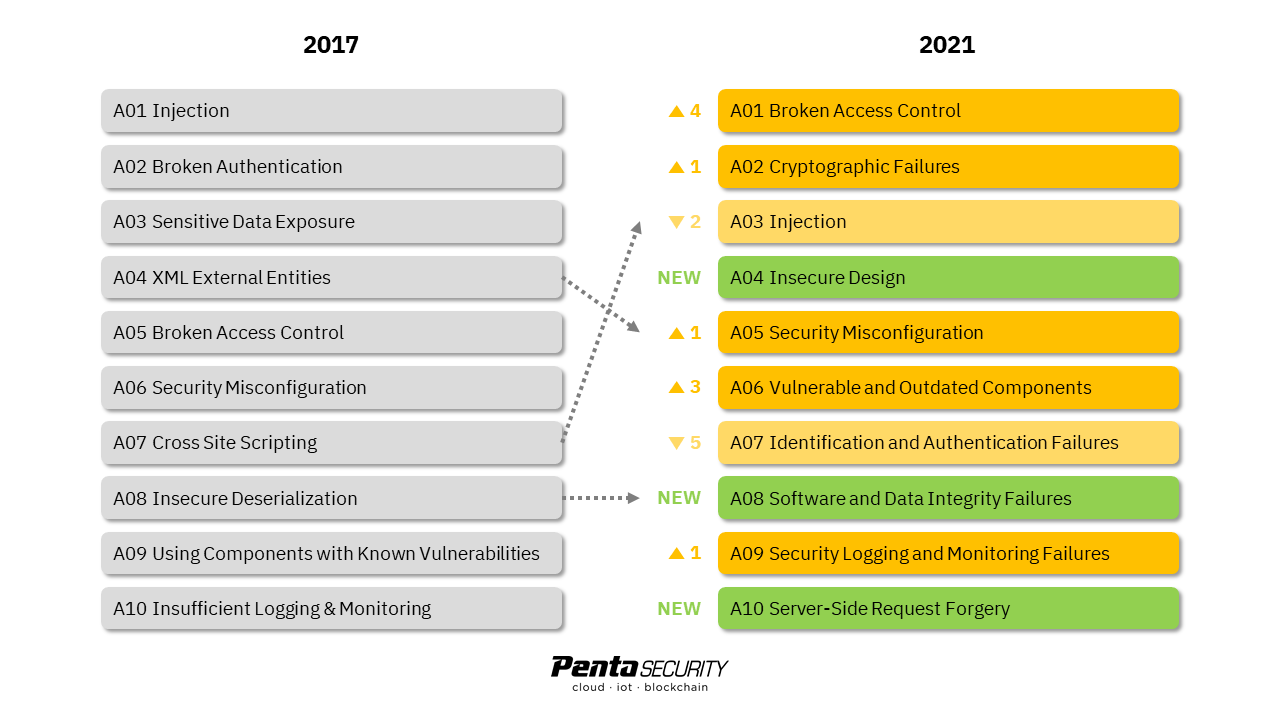
Source: OWASP Foundation
Top 10 Web Application Security Risks Explained
A01. Broken Access Control
Normally, every user account is subject to an access control policy that controls the user’s privileges and permissions. Broken Access Control is when the access control policy fails to limit the user’s account to its intended permissions. In other words, this failure allows the user to access parts of the network that should have been locked from them. By exploiting this vulnerability, hackers could view, modify, exfiltrate, and delete the data of other users and administrators, as well as modify account privileges and permissions to install malware into systems.
Up four spots from the previous ranking, Broken Access Control is now the most critical web application security risk, with over 94% of applications vulnerable and a 3.81% incidence occurrence rate.
Prevention. To protect applications against Broken Access Control, organizations should deny access to functionalities by default and use role-based authentication.
A02. Cryptographic Failures
Cryptographic Failures was formerly known as Sensitive data Exposure on the 2017 list. The term was reframed because Sensitive Data Exposure is merely the consequence caused by Cryptographic Failures. Moreover, it also signals that password protection is no longer sufficient, and that encryption should be applied by default for all databases containing sensitive information.
Prevention. Clearly, the best way to prevent Cryptographic Failures is to use a trusted encryption solution, because manual encryption tends to be weak against today’s sophisticated decipher tools. Penta Security’s D’Amo provides robust encryption using a variety of cryptographic technologies, protecting each layer of the IT system while allowing for column-level encryption and database search.
A03. Injection
Injection is one of the oldest and most widely deployed web attacks. In an injection attack, the hacker injects a malicious code into the system to launch unauthorized commands that request sensitive data. There is a long list of injection attacks, including SQL injection, cross site scripting (XSS), template injection, XPath injection, email header injection, shell injection, and more.
As the all-time “winner”, Injection was ranked first four times in a row in 2007*, 2010, 2013, and 2017. This time, Injection slightly declined to the third position due to the rise of more advanced attack mechanisms. Cross Site Scripting, which was previously ranked independently, also got combined into Injection. Still, Injection remains one of the most common web attacks, with 94% of applications vulnerable and an incidence occurrence rate of 3.37%.
Prevention. To prevent Injection, software developers should eliminate user-supplied input and replace it with mobile OTP, biometrics authentication, dropdown options, and use third-party payment platforms. Indeed, this may sound simple but can be hard to implement for everyone. Hence, another more convenient way is to use a web application firewall (WAF). Penta security’s WAPPLES is an advanced WAF that runs on logic-based rules incorporated with AI algorithms, protecting web applications and APIs from intrusion.
(*In 2007, Injection Flaws came second after Cross Site Scripting, which is also considered a type of Injection under today’s standard.)
A04. Insecure Design
Insecure Design is a new item added to the 2021 list, defining the risks associated with application design flaws. These are not necessarily design mistakes, but simply loopholes that people can exploit to cause damage. This is not to be confused with insecure configuration and implementation. Take a simplified example; a website allows the first 1,000 unique visitors to receive a discount. A malicious actor could use different IP addresses to purchase multiple discounted products and resell them for a gain.
Prevention. It is advised for software developers to use secure design patterns and reference architectures to build applications. Organizations should store a library of these secure patterns and references for future use. If possible, build a red team that performs threat modeling and penetration testing to the application prior to finalizing the design.
A05. Security Misconfiguration
Up one spot from the previous ranking, Security Misconfiguration is the general term that describes the failure in implementing all necessary security controls for an application. The most common cause of Security Misconfiguration is when the system administrator does not change the default settings, or that they forget to reclose the systems after opening them up for testing. For instance, one of the leading causes of sensitive data exposure is misconfigured permissions on cloud storage.
Prevention. To prevent Security Misconfiguration, organizations should disable all unnecessary features, privileges, and permissions by default, and only enable these to those who need them. It is also crucial to periodically review system configurations every time an update or patch is installed, with an emphasis on cloud services and storage.
A06. Vulnerable and Outdated Components
Vulnerable and Outdated Components rose three spots from the previous ranking. This describes the situation where components in a network contain known vulnerabilities that are not patched. This commonly comes in the form of outdated and unsupported operating systems, applications, web application servers, APIs, and database management systems (DBMS).
Prevention. The best way to eliminate Vulnerable and Outdated Components is to perform regular scans for vulnerabilities and ensure that all software components are updated and patched. IT administrators should also manage software components and delete unnecessary programs and features.
A07. Identification and Authentication Failures
Formerly known as Broken Authentication, Identification and Authentication Failures declined the most from the second to the seventh position. This is mostly because companies are increasingly adopting multi-factor authentication (MFA) with advanced authentication techniques like mobile OTP and biometrics, all of which are helpful against social engineering, credential stuffing, and brute force attacks.
Prevention. Before it is too late, it is crucial for all organizations to adopt MFA. Penta Security’s iSIGN+ is an identity and access management solution that provides single sign-on (SSO) MFA with all types of advanced authentication methods, showing that robust identity management does not have to come at the expense of convenience.
A08. Software and Data Integrity Failures
Another new item added to the list, Software and Data Integrity Failures is when certain decisions are made with tampered or corrupted data due to the lack of a data integrity verification process. An example of this is when hackers corrupt a software update file with malware, while the application program automatically installs the update without verifying that the file is original. This was the main cause of the SolarWinds supply chain attack that impacted tens of thousands of organizations worldwide.
Prevention. To protect against corrupted data, digital signatures using PKI-based verification should be in place to verify the authenticity and integrity of critical files. It is also crucial to have a verification process for any code or configuration changes to ensure that external actors cannot modify the code to introduce malware into the system.
A09. Security Logging and Monitoring Failures
Previously referred to as Insufficient Logging and Monitoring, Security Logging and Monitoring Failures describes the failure for the intrusion monitoring and reporting system to catch and report signs of intrusion. This could be because certain audible events are not logged or that the logs are only stored locally, or perhaps the alert threshold is inadequate. Without sufficient reporting, data breaches can remain undetected for months or years.
Prevention. To prevent inadequate logging and monitoring, security administrators must ensure that all failed login attempts and server-side input validations are logged and reported immediately.
A10. Server-Side Request Forgery
As the last item on the list, Server-Side Request Forgery (SSRF) is also newly introduced in 2021. It happens when the hacker uses remote URLs to induce the server-side application to send HTTP requests to other internal services. These corrupted requests could lead to data exfiltration. With the increase in cloud-based web applications, SSRF attacks could result in more severe consequences.
Prevention. The best way to prevent SSRF is to configure network access control policies to have them block all external traffic by default. At the application layer, it is advised to have an allow list for client-supplied input data.
WAPPLES, Trusted Protection Against OWASP Top 10
Despite knowing the risks, it can be overwhelming for many organizations to manage all ten web application risks by implementing all countermeasures and keeping track of them at all times. A third-generation web application firewall (WAF) like Penta Security’s WAPPLES makes it easier than ever to defend against OWASP Top 10.
Unlike most WAFs in the market, WAPPLES’ in-house developed COCEPTM engine runs on algorithm-based detection rules instead of convention signature lists, enabling the detection of all kinds of known and zero-day attacks against web applications and APIs, while achieving a near-zero false positive rate.
Learn more about WAPPLES by downloading its datasheet.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D’Amo
Identity and Access Management: iSIGN+
Car, Energy, Factory, City Solutions: Penta IoT Security
