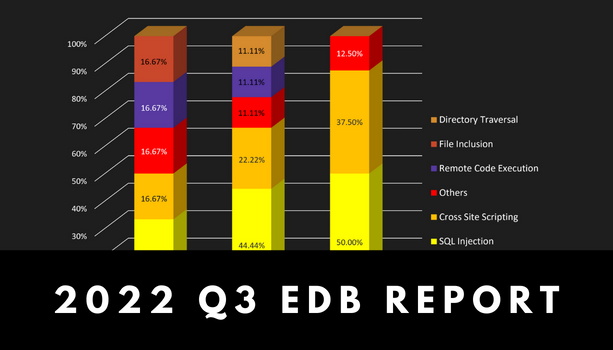
The overall number of web vulnerabilities during the third quarter of 2022 remains relatively low, […]
Read moreAll posts tagged: web attack
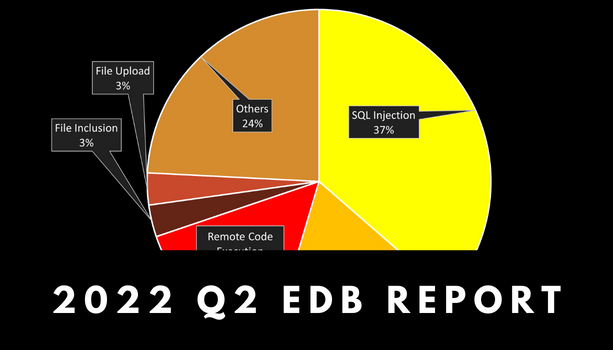
Infographic: Web Vulnerabilities in Q2 2022
The overall number of web vulnerabilities during the second quarter of 2022 decreased significantly from […]
Read moreInfographic: Web Vulnerabilities in Q4 2021
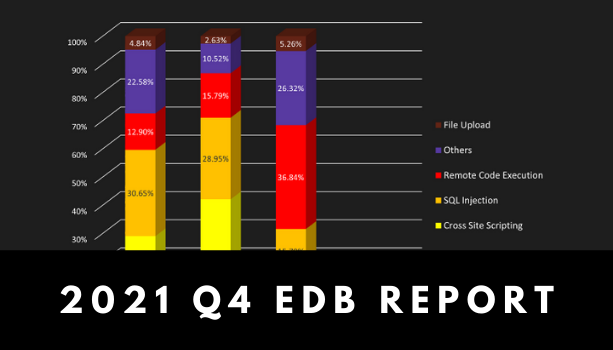
We saw a downward trend in the overall number of web vulnerabilities during the last […]
Read moreInfographic: Web Vulnerability Trends in Q3 2021
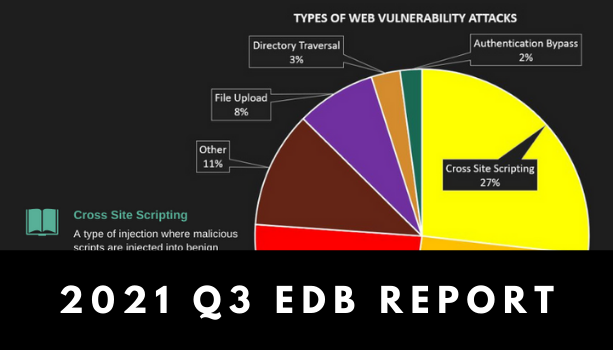
There was overall a slight decrease in the number of reported web vulnerabilities during the […]
Read moreAll You Need to Know About the 2021 OWASP Top 10 Update
The 2021 OWASP Top 10 Cyberattacks on web applications have become more intense and sophisticated, […]
Read moreInfographic: Web Vulnerability Trends in Q2 2021
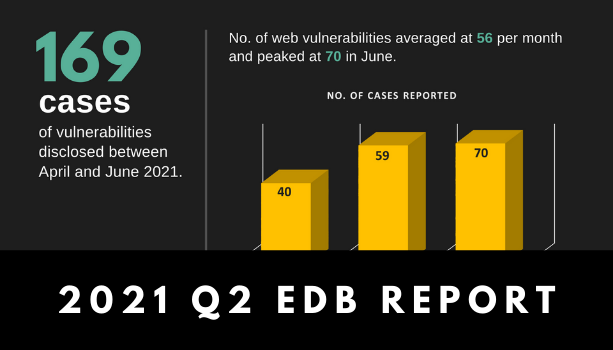
The number of reported web vulnerabilities increased throughout the second quarter, with a significantly higher […]
Read moreInfographic: Web Vulnerability Trends in Q1 2021
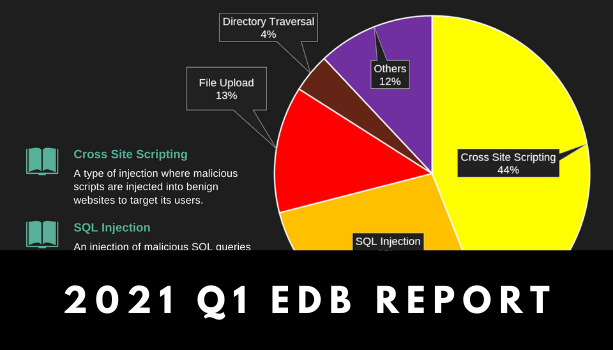
A significant number of web vulnerabilities were reported in January 2021. Among them, cross site […]
Read moreInfographic: Security Trends and Risks in the 4th Quarter of 2020
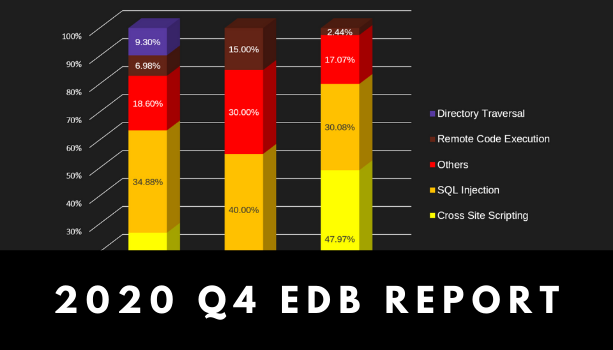
As 2020 came to an end, we saw a significant rise in the number of […]
Read morePenta Security Releases Major Web Attack Trends Report for 2020
SEOUL, South Korea, Dec. 9, 2020 — On December 9th, Penta Security released its annual Web Application […]
Read moreInfographic: Security Trends and Risks in the 3rd Quarter of 2020
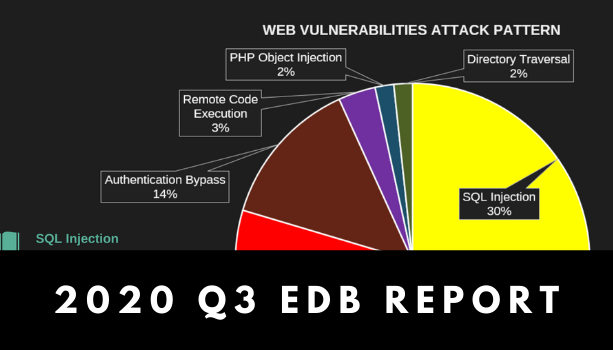
Compared to previous quarters, we witnessed an overall decrease in the cases of vulnerabilities in […]
Read more