Signature-Based vs. Rule-Based WAFs: A Detailed Comparison
Two Types of WAF Threat Detection Systems
To help consumers make more informed choices on web application firewalls (WAF), we discussed in our previous article about the pros and cons of hardware-based, software-based, and cloud-based WAFs. For those who missed it, read here: 3 Types of Web Application Firewalls: How to Choose?
This time, we continue with our guide by comparing two types of threat detection systems used by different WAF service providers: signature-based detection and rule-based detection. Despite serving the same purpose, their operating mechanisms are quite different. Let’s take a look at each.
Signature-Based Detection
The security policies of most WAFs in the market are defined by a list of signatures. Each signature contains a pattern that is a component of a known attack. The WAF would compare every client request and server response against the signatures to identify any potential matches. If a matching pattern is detected, it would either issue an alert or block the traffic entirely, based on the security policies set in place.
Advantages of signatures
Signature-based security policies have been the traditional practice used by firewalls and antivirus programs. The main advantage of having signatures is that it is easy for the WAF service providers to create and update them when new attacks are discovered.
Moreover, since one signature typically defines one specific attack pattern, the operating mechanism is straightforward, making it extremely effective when a user only wants to block a specific attack from a specific location. This also translates to a low rate of false positives because only specific attack patterns are defined.
Disadvantages of signatures
Speaking of updates, every time a new attack pattern is discovered, a new signature must be added to the list, making it necessary to receive timely updates. With countless numbers of new attacks turning up each year, a typical signature-based WAF runs on thousands of signatures.
Yet, it is impossible to include all signatures in a set of security policies because that would take up a ton of server resources, greatly undermining processing speed and application performance. Moreover, having an excess amount of unnecessary signatures also increases the chance of blocking legitimate traffic, raising the false positive rate.
Keeping only relevant and necessary signatures in a policy is ideal. But it is very difficult to keep the right balance. This is why some service providers use machine learning to study the application environment for a couple of weeks during initial deployment as an attempt to create an optimized security policy. However, this doesn’t always promise optimized results and raises the cost of the deployment.
Rule-Based Detection
Rule-based threat detection is an emerging new approach in the WAF market, made possible by artificial intelligence. Compared to signature-based detection, it relies more on technology and less on manual interventions. Here is why.
Commonly, a signature is created by recording the syntax of the source code of an attack. On the other hand, a rule is not defined by directly recording the pattern of an attack. Using artificial intelligence, a rule is derived from a number of attack patterns, in which an inference engine is used to analyze the syntax patterns to deduce a condense and representative rule. As such, a single rule can define as many attacks as hundreds of signatures can. Think of a rule as a pattern of patterns (see figure for simplified illustration).
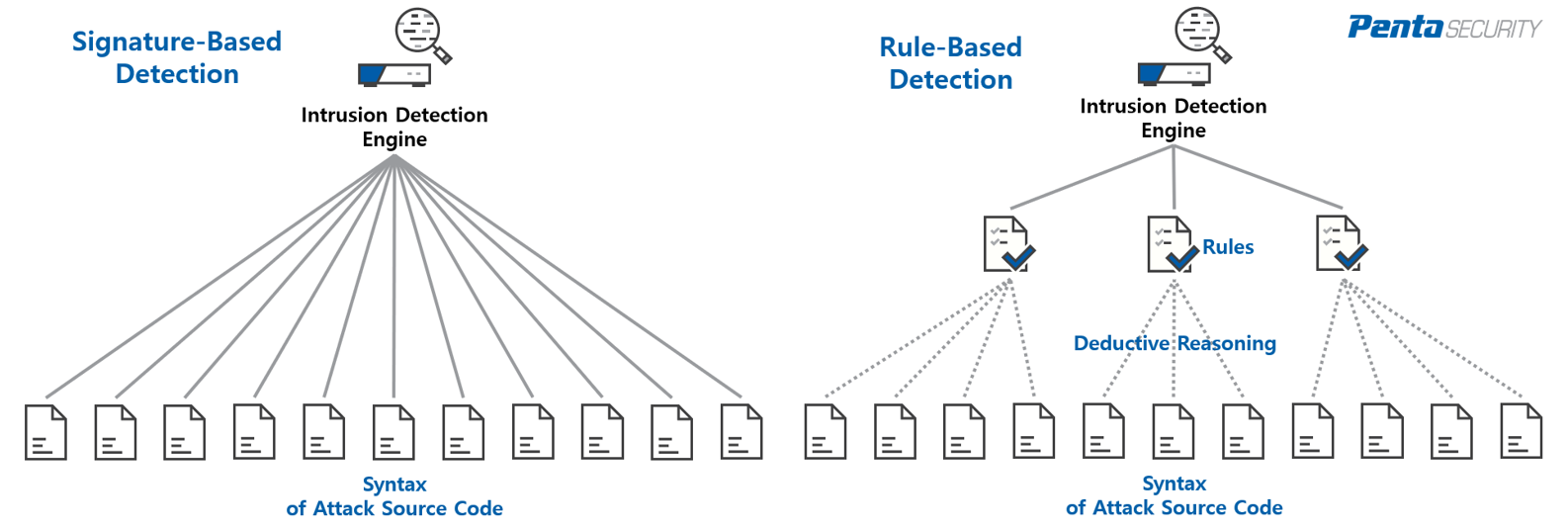
Note that the figure is only a simplified explanation. In reality, a rule can be derived from not only the source code, but also from specific targeted networks, because even the same attack can leave different networks looking differently.
Advantages of rules
Depending on the application environment, a signature-based security policy runs on over 2,000 to 8,000 signatures, while a rule-based security policy only requires a few dozen rules to detect an equivalent amount of attacks.
Clearly, the greatest advantage of a rule-based WAF is speed and performance. Based on the results of a series of internal tests conducted by Penta Security’s research team, on average, a rule-based WAF with 27 rules in place successfully blocked 95% of attacks, equivalent to the result of a signature-based WAF applying 8,000 signatures. On the performance side, when 27 rules were applied, a 20% reduction of processing speed was observed, while with 8,000 signatures in place, processing speed dropped by 50%.
Another key advantage is that rule-based WAFs are extremely easy to maintain. Once an initial set of rules are set in place, almost no additional manual updates are required. The service provider would update existing rules and add new rules to the list when necessary.
A rule-based WAF can also block certain zero-day attacks because it is likely that a simple change in attack pattern would not escape the rules.
Disadvantages of rules
Some prefer signature-based detection systems as they are more conservative and leave more room for manual intervention. Indeed, rule-based detection systems rely more on artificial intelligence, leaving some to feel a sense of lack of control.
Those who are so used to seeing signature lists could feel skeptical about how few the number of rules are needed. However, consistent with lab testing results, real-world comparisons do not show any lack of detection capabilities by rule-based systems.
WAPPLES, a rule-based next-gen WAF
WAPPLES is a logical web application firewall based on artificial intelligence. Run by its patented rule-based detection engine COCEPTM, WAPPLES currently possesses a pool of more than 30 rules that can be fine-tuned to create robust custom security policies.
WAPPLES’ rules are sophisticatedly defined by logically analyzing the attack patterns of millions of attacks, making it effective even against zero-day attacks. Periodic updates and self-diagnostics keep it at its best state ready for the newest threats.
Equipped with a load balancer, WAPPLES is available in both hardware and software forms, protecting on-premises and cloud-based servers.
To learn more about WAPPLES, click here.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D’Amo
Identity and Access Management: ISign+
Car, Energy, Factory, City Solutions: Penta IoT Security
