6 Types of Email Threats and How to Mitigate Them
Despite the popularity of instant messaging apps and social media, email remains to be the most used medium for formal communication, especially for organizations. This makes the email system highly susceptible to cyber threats.
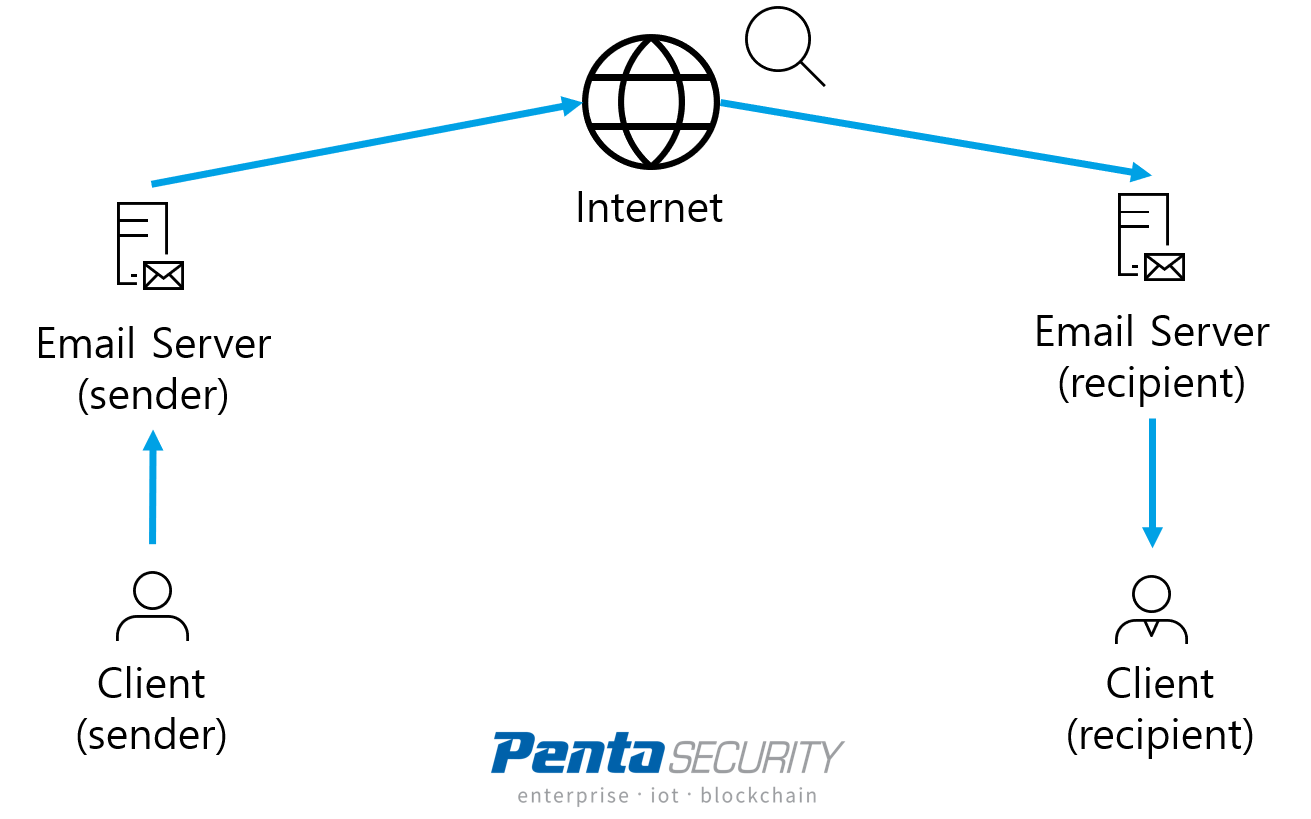
Just how exactly does email work? An email system consists of clients and servers. A user composes, sends, and receives emails using the client. After a user sends an email, the message gets encrypted and broken down into smaller pieces, then gets transferred via the network to the email server. The server then delivers the encrypted message over the Internet. Finally, the receiver’s email server picks up the message by searching for addresses matching its clients. Thus, to keep email messages safe, the client, server, as well as internal network infrastructure must all be secured.
Securing email is especially crucial for organizations because a work inbox contains countless amounts of sensitive corporate information, including financial and operational information, legal information, and even trade secrets. Moreover, employees tend to be less cautious when handling corporate information compared to their personal information. Many may send passwords and even credit card numbers over email.
Many companies, especially large enterprises and financial institutions, adopt their own email servers in order to control where exactly their data are and to keep their data secure. However, even that does not prevent companies from suffering data breaches because threat actors have a variety of methods to attack the email system.
In this article, we will outline some of the common tactics used by attackers to target the email system, as well as some advice on how to mitigate these threats.
Types of Email Threats
1. Malware Delivery via Spam
Malware is one of the most serious yet common threats that are commonly delivered through emails. This technique is especially successful at targeting employees within organizations. By sending spam mail impersonating legitimate senders such as customers, partners, or suppliers, victims are easily tricked into downloading rogue files that contain malware. Most of the time, the victims do not realize that they are installing malware onto their computers because signs of intrusion do not occur right away. The attackers can silently take control of the victim’s computer, then sneak through the corporate IT network to spread the malware into nearby systems until eventually, the entire IT infrastructure becomes infected, a process that can take days or even months. During this time, it would be lucky if the organization discovers the malware at the early stages. Yet, oftentimes, the intrusion is only detected after significant parts of the IT system have already been compromised, with servers encrypted and sensitive data leaked.
2. Credential Theft via Phishing Emails
Phishing emails are very similar to spam, except that they are more customized and more often than not used to deceive victims into giving up sensitive information directly. For example, attackers could somehow acquire a list of customer data from a financial institution, possibly leaked from a previous data breach. The list may contain the customers’ names, email addresses, bank account numbers, and perhaps other personal information. The attackers then may use such a list to craft highly convincing spear-phishing emails to lure the victims into clicking a fake link that requires them to fill in their online banking login credentials. Similar attacks can be done to company employees by tricking them into giving out credentials for corporate admin accounts.
3. Business Email Compromise
Business email compromise (BEC) is a highly sophisticated type of spear phishing that targets high-ranking employees at the targeted organization, hence also commonly referred to as “CEO fraud”. Different from other phishing attacks, in a BEC attack, the attackers invest a lot of time to study the victim’s habits and behaviours, and gain information on the recent events they are involved in from their social media activities. After gaining all the information, a highly realistic email would be sent to the victim. For instance, after knowing that the victim is recently involved in negotiating a partnership opportunity with a particular person at a particular company. The email would impersonate that person with details of the negotiation while cc’ing a manager at the finance department to transfer funds into their account as an upfront deposit. With such specific details and accurate email addresses, it is almost impossible for the victim to notice any flaw. Thus BEC is commonly used to steal money and trade secrets.
4. Malicious Bot and DDoS Attacks
Just like how a traditional DDoS attack crashes the victim’s web server, attackers can use hijacked botnets to send out a massive amount of emails to a targeted organization, causing the email server to crash from system overload. DDoS attacks on web servers are more common in B2C businesses as they rely on their websites for generating sales, while DDoS attacks on email servers tend to target B2B businesses because a large portion of their sales is conducted via email communication.
5. Authentication Attacks on Email Servers
Sometimes, the email inbox itself can become the target of attackers. In this case, attackers would try to launch authentication attacks on the email servers by using brute force, credential stuffing, and other methods to break over authentication and gain access to the email server. This would grant the attackers access to all the email messages and attachments stored in the server.
6. Vulnerabilities in Email Servers
Recently, four zero-day vulnerabilities found in Microsoft Exchange Server were exploited by alleged Chinese state-sponsored hackers. This was later discovered to have compromised over 30,000 servers affecting more than 100,000 organizations worldwide, leaking millions of emails. Indeed, a compromise of the email server is a catastrophic event not only due to the exposure of email messages, but also because hackers can easily infect nearby IT systems by traveling through the internal network.
How to Mitigate Email Threats?
To keep an email system safe, it is necessary to secure both the client and the server. Security on the client side is more dependent on the users’ awareness of potential threats. Thus, it is important to keep employees educated and informed about spam and phishing attacks. However, there are limitations to how well a person can identify spam and phishing emails, especially as they become increasingly sophisticated.
This is why it is equally important to secure the server side so that spam gets filtered and DDoS attacks do not go through. Email security tools also help scan for attachments infected with malware. It is also helpful to have a load balancer to keep the email servers stable, preventing system overload from affecting performance. Lastly, it is crucial to keep email servers up to date with the latest patches to prevent any attacks that exploit software vulnerabilities.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D’Amo
Identity and Access Management: ISign+
Car, Energy, Factory, City Solutions: Penta IoT Security
