Although web encryption has been around for the past few decades, it only became a […]
Read moreAll posts tagged: firewall
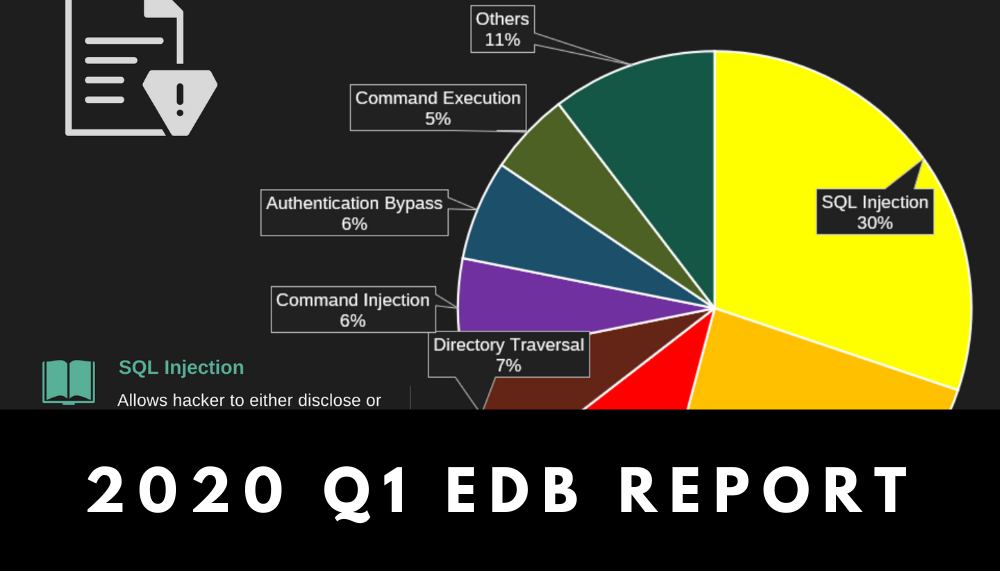
Infographic: Security Trends and Risks in the 1st Quarter of 2020
The first quarter of 2020 has been chaotic. As COVID-19 continues to disrupt social and […]
Read moreSo Long, Windows 7!
Microsoft has ended its official support for Windows 7 on 14th January 2020. What does […]
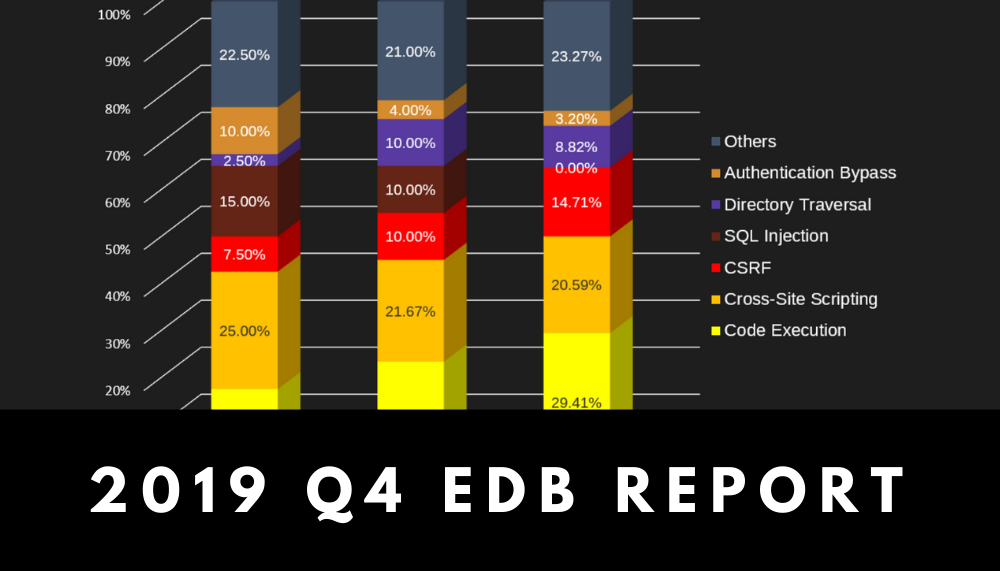
Read moreInfographic: Security Trends and Risks in the 4th Quarter of 2019
Latest report on web security trend is available! Have a look at the infographic below […]
Read moreInfographic: Security Trends and Risks in the 3rd Quarter of 2019
Wondering about the most recent trends in web security? See the report below for an […]
Read moreWhat We Can Learn from Georgia’s Massive Cyberattack and Do Better
It was just last week, on the 28th of October, that we were shocked […]
Read moreInfographic: 2019 Cybersecurity Fun Facts
All crucial cybersecurity-related trends you need to know about in 2019: Get to know […]
Read more3 Massive Data Breaches that Could Have Been Easily Avoided
These days, many consider data to be the most valuable asset of any organization with […]
Read moreWhat is AEP (Advanced Endpoint Protection)?
Although they were once considered reliable and accessible, traditional AV (anti-virus) programs are now considered […]
Read morePCI DSS and the Road to Compliance
When you’re in the world of cyber security and researching new products, there’s no doubt […]
Read more