How Does Public Key Infrastructure (PKI) Work? An Easy Guide
What is public key infrastructure (PKI)?
Public key infrastructure, or PKI – despite being a frequently used term, the mechanisms behind it can be quite difficult to understand. In this article, we explain PKI in the simplest language possible by walking through the technology step by step.
Encryption and Authentication
First and foremost, what is PKI? PKI is a general term that defines the technology used to encrypt and authenticate data during transmissions. Encryption makes the data unreadable, allowing only authorized entities to decrypt (i.e. read) them. Authentication ensures data integrity by proving that 1) the data is not modified during transmission, and that 2) the sender of the data is who they claim to be.
PKI’s usage for authentication
To explain how PKI works, we need to start by explaining its usage for authentication. As mentioned above, authentication is the process of verifying the integrity of data and the identity of the sender. This is done through a digital certificate.
Digital Certificates
In the digital world, each entity is associated with a digital certificate that serves as its identity. An entity does not have to be a person or a device, it can literally be anything, like a software program, a process, or even an action. Just as how we prove our identity in the real world with passports and photo IDs, in the digital world, a digital certificate does the job.
Certified Authorities
Now you may ask, how do we know that the digital certificates are legitimate? Let’s go back to the real world – how does border control know that your passports are legitimate? The booklet itself does not provide any legitimacy, but the fact that the passport is issued by your country’s government does. In this case, the government is the certified authority.
The same process applies to a digital certificate. Let’s say you want to log in to your online banking account. In this case, you, as the client, is sending a request to the bank’s server to retrieve your account information and display it through the web application. In this process, the bank’s server verifies your digital certificate generated by the certified authority (CA) trusted by the bank. (Just as how the immigration officer trusts your passport’s issuance authority.) Certified authorities are usually third-party firms that specialize in generating digital certificates.
For example, Penta Security’s ISign+ is a certified authority that issues digital certificates trusted by many financial institutions. It also secures accounts by providing single-sign-on, multi-factor authentication for businesses across the world. To learn more about ISign+, click here.
How Does PKI Authenticate Digital Certificates?
PKI works by encrypting data (in this case, digital certificate) with a cryptographic key, while having a separate key for decrypting it. The point here is to have one key for encryption and another for decryption. One of them is a private key, held by the key owner, while the other is a public key, shared with the public. Depending on the usage, the private key can either be the encryption key or the decryption key.
In this case of authenticating a digital certificate, the private key would be an encryption key held by the owner of the digital certificate, while the public key would be a description key given to whoever that requests verification of the owner’s identity.
The process works like this. The owner of the certificate first encrypts it with the private key, then hands over the public key to the bank. The bank would decrypt it with the public key and verify the owner’s identity, and authenticate the user to access their account.
The magic here is that the decryption key can only decrypt the exact same data that the encryption key has encrypted. This means that if the decryption key can successfully decrypt a set of data, the integrity of the data can be verified. Had the data been illegally modified by unauthorized parties in the transmission process, the decryption key would fail to decrypt the data (see figure 1).
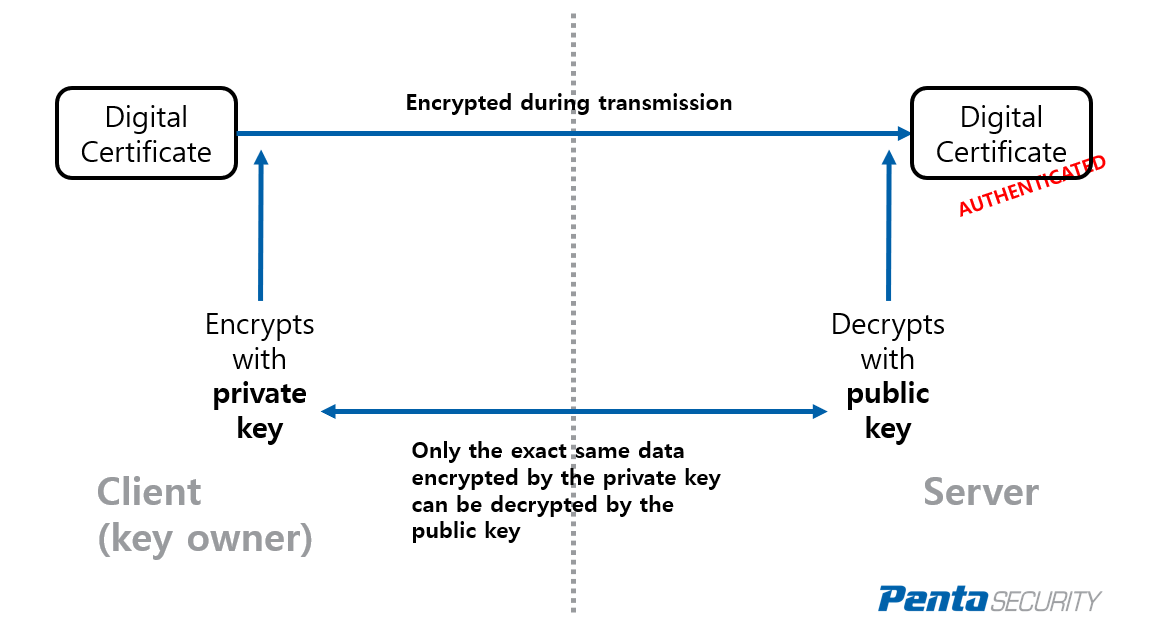
<Figure 1. PKI’s usage for authentication>
{SPACE}
Other usages of PKI
How Does PKI Secure Private Messages?
Now imagine another situation where Aiden needs to send a confidential message to Bob. In this case, there are three things that Aiden and Bob would want to watch out for:
1) The message is kept secret so that no third party can view it during transmission.
2) The message is not altered or modified by any third party during transmission.
3) When Bob receives the message, he needs to make sure that the sender is truly Aiden, and not someone who is pretending to be Aiden.
PKI can easily ensure all these three criteria are met. How does it work in this case? First, Aiden needs to request Bob’s public key. Then Aiden uses Bob’s public key to encrypt the message he wants to send. After Bob receives the message, he simply needs to decrypt it with his private key. Note that different from the case of authenticating digital certificates, in this case, the owner of the keys is the receiver, not the sender, and that the public key is used as the encryption key while the private key is used as the decryption key (see figure 2).
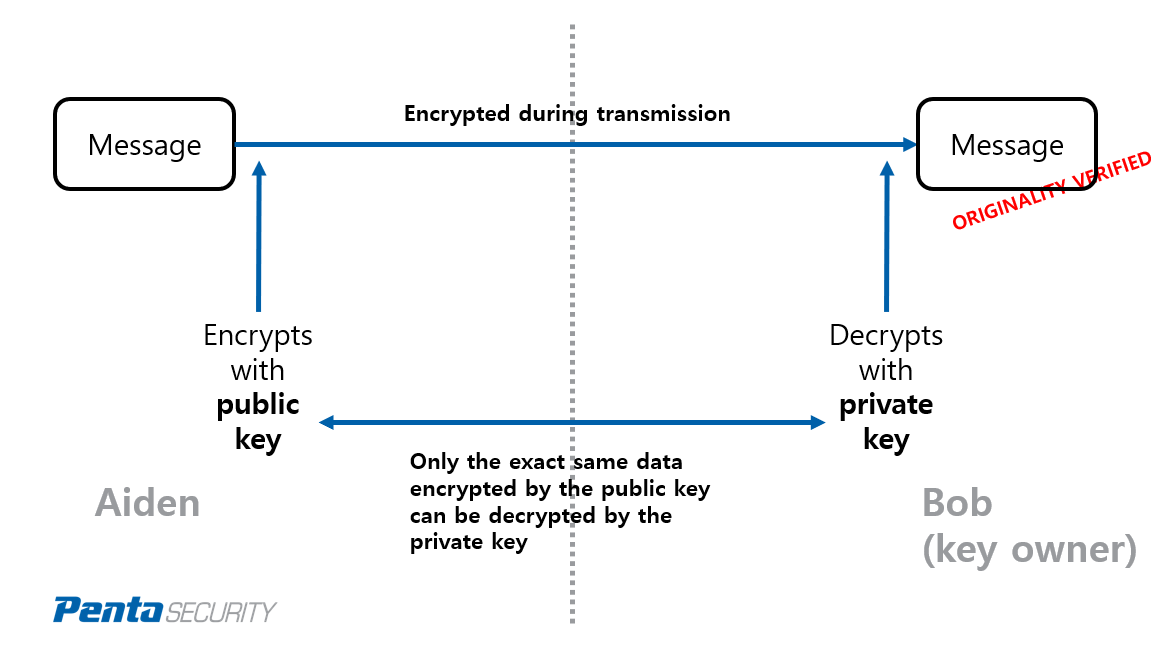
<Figure 2. PKI’s usage for securing private messages>
{SPACE}
Other than the two examples above, PKI can be used for securing retail transactions, digitally signing applications, smart card authentication, and many more.
Penta Security’s ISign+ PKI offers authentication and end-to-end encryption, helping businesses secure all kinds of data transmission processes including monetary transactions, IoT connections, private messages, and so on. Learn more about ISign+ here.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Web Application Firewall for Cloud: WAPPLES SA
Database Encryption: D’Amo
Authentication: ISign+
Smart Car Security: AutoCrypt
