The Benefits of Using a Database Encryption Solution
Data Encryption: the Last Line of Defence
Data encryption is unique in its approach when compared to the other cybersecurity measures such as antivirus programs, web application firewalls, and identity and access management systems. All the other security tools are aimed at preventing malicious outsiders from entering the IT system, whereas encryption protects the data itself, so that even if all other measures fail and attackers happen to gain access to the data, it provides no value to them. In a sense, data encryption is the last line of defence against cyberattacks.
How Does Database Encryption Work?
Most of us are familiar with the meaning of data encryption — plain text gets encrypted into uninterpretable ciphertext, and can only be accessed and decrypted by authorized users who hold the encryption key.
What we are less familiar with is how the database encryption process works in real life. Some of the commonly asked questions are: Does encryption happen before or after the data is transmitted to the database management system (DBMS)? Does encryption slow down the application? How does the database search engine work if the stored data is encrypted?
The answers to these questions would depend on the type of encryption method used. In this blog, we will explain the three types of commonly used encryption methods.
Three Types of Encryption Methods
There is no universally accepted method for database encryption. Some of the common database encryption methods include the API method, plug-in method, and TDE method.
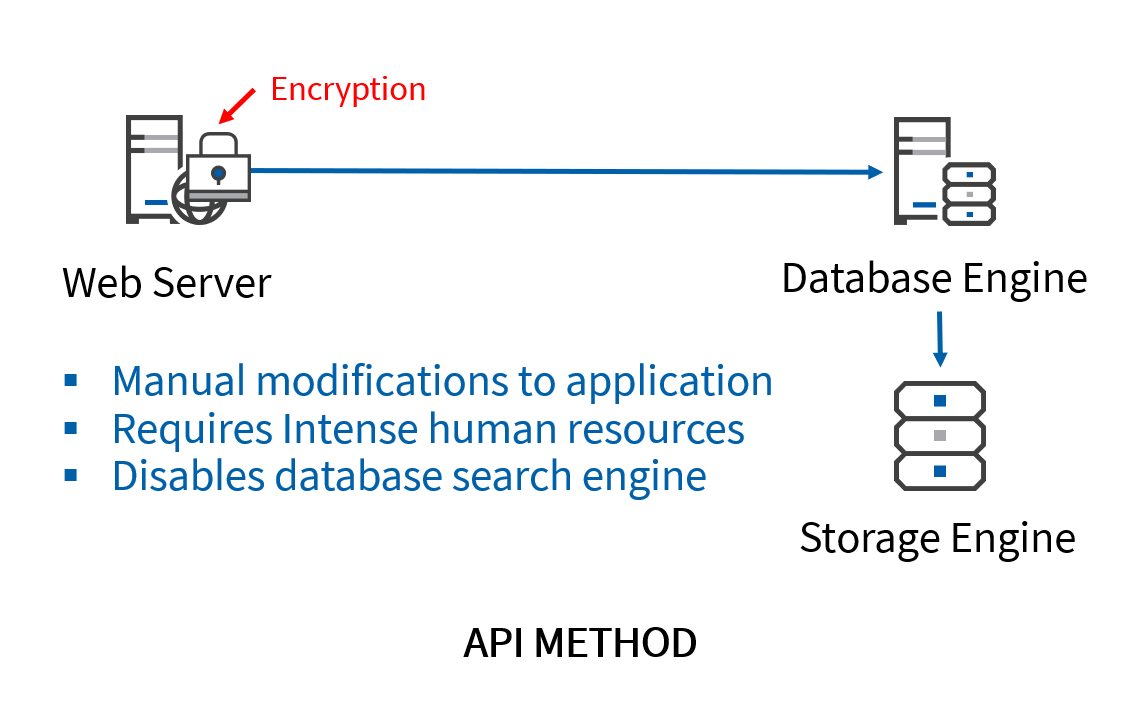
API Method
As the name suggests, the API (application programming interface) method encrypts data at the application level. An engineer would need to manually edit the queries that are referenced to the encrypted columns from inside the application. Since encryption is conducted before the data is transmitted to the DBMS, this method is applicable regardless of the DBMS used. Instead of adopting any third-party solutions, organizations that use the API method hire their own staff dedicated to data encryption.
However, for organizations that handle large amounts of data, this method can be extremely inefficient and costly as it requires a lot of time and human resources. The API method is also unsustainable because time and effort would need to be constantly readjusted based on the fluctuations of the amount of processed data. More importantly, modifying the queries inside the application could easily lead to application issues and significant performance slowdowns. Lastly, application-level encryption disables the search capabilities of the DBMS because the data is already encrypted beforehand.
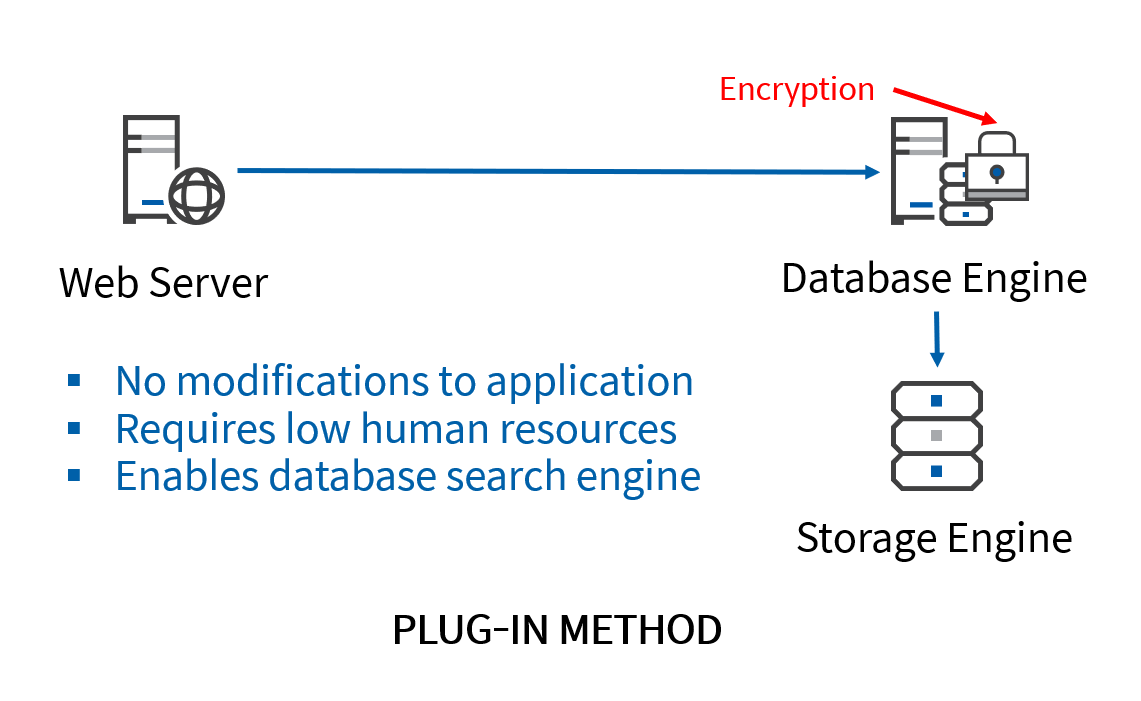
Plug-In Method
Under the plug-in method, the encryption process occurs at the database engine level. An encryption module is attached as a plug-in to the database engine of the DBMS. Opposite to the API method, the encryption process is independent of the application, and thus does not pose any impact on application performance. It also requires very few manual modifications.
The plug-in method is mostly conducted by encryption modules provided by third-party vendors. These will likely allow for column-level encryption, meaning that the users can select only the sensitive columns within a database to encrypt. They are also accompanied by access control and auditing features, allowing for the system administrators to monitor any unauthorized access attempts.
Penta Security’s D’Amo is an encryption module that utilizes the plug-in method. The entire encryption process occurs within the DBMS at the database engine level, hence the data is still searchable from the database search engine. D’Amo is compatible with the majority of DBMSs used by organizations around the world.
Read the success story of a major financial institution adopting D’Amo.
To learn more about D’Amo, click here.
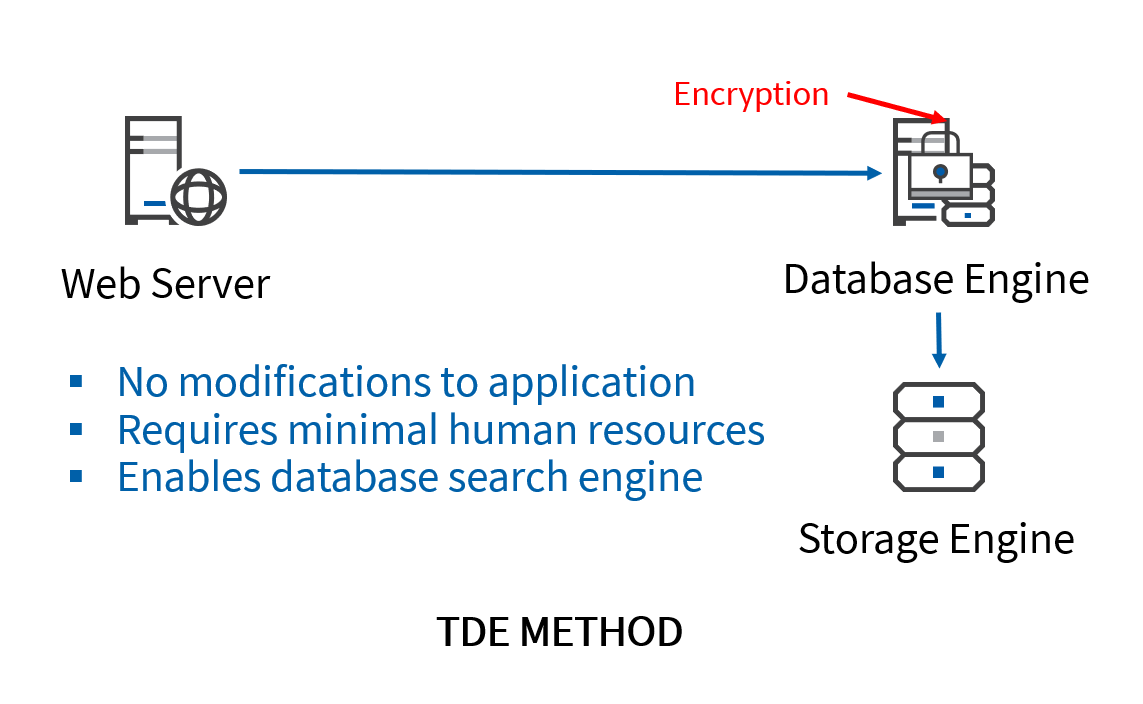
TDE Method
Transparent data encryption (TDE) is similar to the plug-in method, but instead of attaching a plug-in, a software-based encryption module is installed directly into the database engine. Along with all the features and benefits of a plug-in module, this method further eliminates any need for manual modification to the database or application.
MyDiamo is a software-based encryption module that can be installed directly into all major open-source DBMSs including MySQL, PostgreSQL, and MariaDB. While a free version is available for individual users and non-profit causes, a paid license is available for commercial use, popular among the healthcare, educational, and financial sectors.
To learn more about MyDiamo, click here.
The Benefits of Using an Encryption Solution
Clearly, instead of doing things manually with the API method, adopting an encryption solution that utilizes the plug-in or TDE method offers countless benefits. Not only does it save time and resources, by also offering access control and auditing as a complete package, organizations can safely guard their important data from today’s increasingly sophisticated phishing attacks and ransomware threats.
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D’Amo
Identity and Access Management: ISign+
Car, Energy, Factory, City Solutions: Penta IoT Security
