September 2022, Issue I 1. Samsung suffers second data breach of the year, customer […]
Read moreCurrently browsing: Blog
How to Develop an Effective IAM Strategy
The Importance of IAM Strategy Whereas data encryption serves as the last line of defence […]
Read more[Security Weekly] UK Water Supplier Hit by Clop Ransomware in Mistargeted Attack
August 2022, Issue II 1. UK water supplier hit by Clop ransomware in mistargeted […]
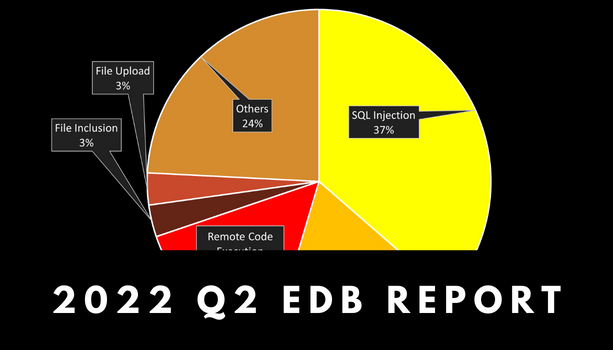
Read moreInfographic: Web Vulnerabilities in Q2 2022
The overall number of web vulnerabilities during the second quarter of 2022 decreased significantly from […]
Read morePenta Security’s One-stop Security Solutions for Enterprises
Over the past decade, cybersecurity has become a board-level issue for businesses and organizations. Security […]
Read more[Security Weekly] Microsoft Enterprise Email Service Targeted in MFA-Bypassing Phishing Campaign
August 2022, Issue I 1. Microsoft Enterprise Email Service targeted in MFA-bypassing phishing campaign […]
Read moreWhat Are API Attacks and How Can You Prevent Them?
Cyberattacks using API (Application Programming Interface) are increasing explosively in recent years. An API is […]
Read more[Security Weekly] Newly Discovered Orbit Malware Creates Stealthy Backdoor on Linux Devices
July 2022, Issue II 1. Newly discovered Orbit malware creates stealthy backdoor on Linux […]
Read moreWhat Is a Reverse Proxy and What Does It Mean to Enterprise Security?
What Is a Proxy Server? At the most fundamental level of internet communication, whenever a […]
Read more[Security Weekly] Killnet Launches Massive DDoS on Lithuania Over Sanctions Against Russia
July 2022, Issue I 1. Killnet launches massive DDoS attacks on Lithuania over sanctions […]
Read more