A Password-Free Enterprise? Pros and Cons of Each Password Alternative
Nearly two decades ago, Bill Gates predicted the death of passwords at the 2004 RSA Conference, with weak security being the primary reason. Since then, this prediction has gained growing popularity, with many industry professionals believing that passwords will very soon be replaced by more reliable and sophisticated authentication methods. Fast forward to 2022, as predicted, we now have a handful of authentication methods as potential password alternatives. But are we finally approaching the end of passwords?
Not quite yet. Today, passwords continue to be the most commonly used authentication method across the globe, for clear reasons – passwords are quick to set up, easy to manage (especially with password managers), and can be used anytime and anywhere.
This isn’t to say that the predictions are wrong. Passwords do come with a lot of security risks. And most account credential hacking attempts are targeted at passwords, such as brute force, credential stuffing, and phishing. To compensate for these risks, it has become common practice for organizations and enterprises to adopt multi-factor authentication (MFA) for account management. In fact, for many organizations regulated by personal data protection laws and standards, MFA is usually a mandatory requirement.
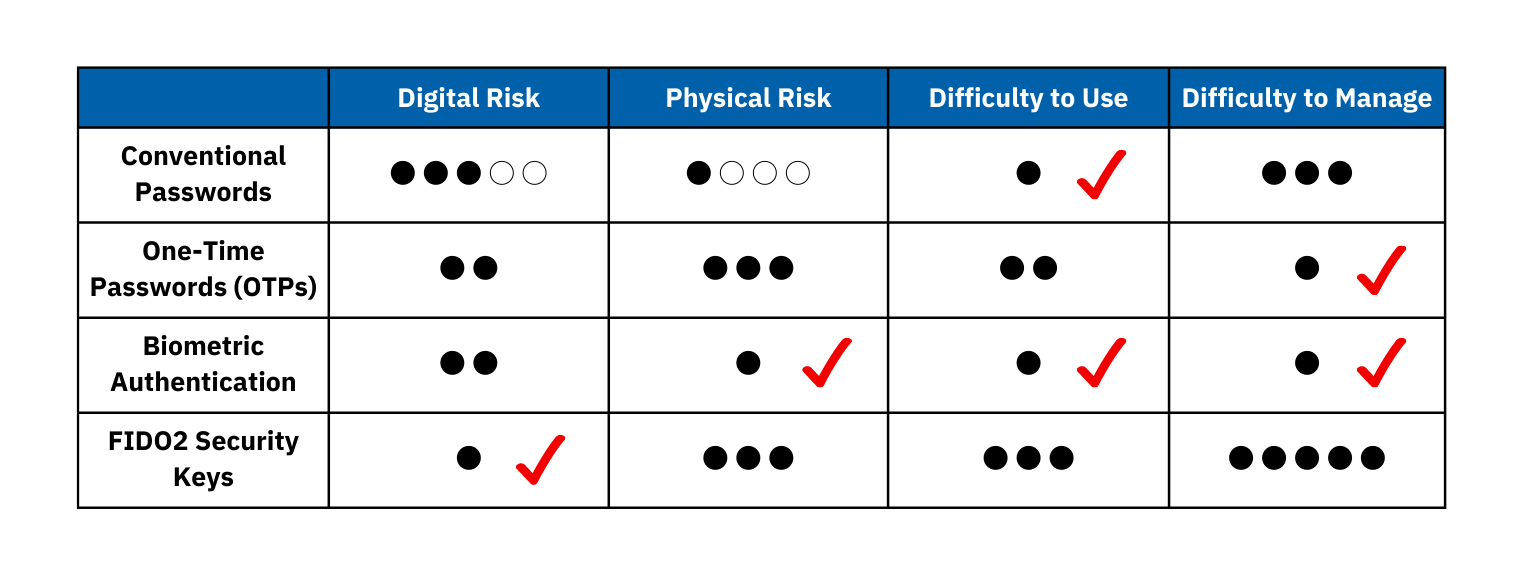
Here we evaluate the pros and cons of several commonly used authentication methods over four different aspects:
1) digital risk – the risk of being hacked,
2) physical risk – the risk of (the authentication device) being lost or stolen,
3) difficulty to use – efficiency and portability, and
4) difficulty to manage – cost and storage.
Conventional Passwords
Digital Risk: O O O ~ O O O O O
Since the majority of account hacking attempts are made to target conventional passwords, the digital risk of using conventional passwords is no doubt the highest among all authentication methods. However, the level of risk varies greatly depending on the user’s password choice. Using robust passwords can reduce the risk of hacking significantly. Here are some tips to create strong passwords: Smart and Creative Ways for Setting Easy and Robust Passwords.
Physical Risk: O ~ O O O O
If the user fully memorizes their passwords and do not record them anywhere else, there is virtually no physical risk involved. However, many users – especially enterprise users – tend to write down their login credentials in their notebook, on a shared spreadsheet, or even on sticky notes, all of which can be easily stolen by others. Hence, the level of physical risk depends heavily on the user’s behaviour.
Difficulty to Use: O
Passwords remain the most popular authentication method due to their ease of use.
Difficulty to Manage: O O O
Despite easy to use, memorizing all passwords is an impossible task. Nevertheless, there are many reliable password managers that safely generate and store passwords for the user.
One-Time Passwords (OTP)
One-time passwords are, as the name suggests, usable only once over a limited time period. During the login process, the user enters their account information to request an OTP, which will then be sent to them via text or email using the pre-registered phone number or email address.
Digital Risk: O O
Depending on the service provider, an OTP is usually valid for only 60 seconds after the message gets sent, making it impossible for any hackers to perform conventional password hacking techniques like brute force and credential stuffing. However, although unhackable through conventional means, it is still possible to gain access to OTPs if hackers have already gained prior access to the user’s phone or email inbox through a prior data breach or hacking operation.
Physical Risk: O O O
It is possible for a threat actor to purposely steal a target’s smartphone or copy the user’s SIM card information in an attempt to receive the OTP. Users could also lose their smartphones, potentially having them end up in the wrong hands.
Difficulty to Use: O O
OTPs are quick and easy to use, but requires the user to have their smartphone with them during the authentication process.
Difficulty to Manage: O
Once registered, OTPs do not require any additional hardware and storage space.
Biometric Authentication
Biometric authentication is an umbrella term for all authentication methods that identify users by recognizing their body parts, such as fingers, eyes, and face. Now becoming one of the most popular alternatives to passwords, fingerprint scanners and facial recognition cameras are commonly built into smartphones and business laptops, and widely used for unlocking devices and authorizing payment transactions.
Digital Risk: O O
Biometric authentication is one of the safest authentication methods today. Yet, it does have its security concerns. Even though corporations like Google and Apple claim that they do not store biometric information, many governments do under certain conditions. As such, some worry that fingerprints and facial scans could potentially be stolen and copied via digital means and reproduced through advanced printing technologies. Nevertheless, replicating and reproducing biometric information is extremely complex, making it very unlikely that any hacker would try.
Physical Risk: O
Physical risk to biometric authentication is non-existent as the user needs to be physically present.
Difficulty to Use: O
The primary reason behind the popularity of biometric authentication is that it is easier to use than conventional passwords and does not require the user to carry any device with them.
Difficulty to Manage: O
Biometric authentication does not require any additional hardware and storage space.
FIDO2 Security Key
Security keys, or security tokens, are physical devices that serve as digital certificates that prove the users’ identity. Usually coming in the form of USB devices that can be directly inserted into the workstation, all security keys must be pre-registered by FIDO2 prior to usage. During the authentication process, the security key sends the public key along with the user’s digital certificate to the service, while keeping the private key within the device.
Digital Risk: O
Security keys keep the generated cryptographic credentials within itself and never store the credentials anywhere else, meaning that hackers have no chance of hacking into these credentials. Moreover, the credentials generated are unique for each service.
Physical Risk: O O O
Despite their advantages in digital security, security keys can be easily lost and stolen.
Difficulty to Use: O O O
Although the authentication process is quick and easy, the user needs to carry around a USB device.
Difficulty to Manage: O O O O O
At the enterprise level, managing hundreds of security keys spread out among employees can be a daunting task. Most likely, some devices will end up missing.
Why Multi-Factor Authentication (MFA) Remains the Optimal Solution
Looking at the summary table, by comparing the four attributes of each authentication method, it is clear that every authentication method has its comparative strengths and weaknesses, and that none of the methods has an absolute advantage over the others. Therefore, it is strongly recommended that enterprises continue to utilize more than one authentication factor for their corporate accounts.
iSIGN+ is an enterprise identity and access management (IAM) system supporting MFA factors including mobile OTPs and biometrics. To reduce the complexity of using multiple authentication factors, iSIGN+ comes with a single sign-on feature that integrates the login credentials of different software and systems within the organization, making credential management both secure and convenient.
For more information on security implementation, check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D’Amo
Identity and Access Management: iSIGN+
Automotive, Energy, Industrial, and Urban Solutions: Penta IoT Security
For detailed inquiries, contact Penta Security’s security consulting team.
