Penta Security Announces Integration with Buy with AWS Penta Security, a leading cyber […]
Read moreAll posts tagged: cloudbric
[Cloud Security] Cloudbric in the Fast-Growing SaaS Market
According to the Korea Software Industry Association (KOSA), the domestic SaaS market is projected to […]
Read morePenta Security Expands Cloudbric Managed Rules for AWS WAF to Two New Regions
Penta Security, a leading cyber security company and provider of web application security […]
Read more[Penta Inside] Welcoming 2025 with Penta Security!
Welcoming 2025 with Penta Security Penta Security kicked off the new year by bringing […]
Read more[Penta Inside] Celebrating 10 Years of Cloudbric
Celebrating 10 Years of Cloudbric Hello! We are Penta Security, a security company based […]
Read morePenta Security Enhances ‘Cloudbric VPN’ with New CLBK Staking Feature
Penta Security, a leading cyber security company and provider of web application […]
Read more[Penta News] Penta Security Revamps Brand Identity to Strengthen Global Market Presence
Penta Security Revamps Brand Identity to Strengthen Global Market Presence Penta Security has undertaken […]
Read morePenta Security Launches a Cloud Security Provider WAF Managed Service on AWS Marketplace
Penta Security Launches a Cloudbric WMS on AWS Marketplace Penta Security Launches a Cloudbric WMS […]
Read morePenta Security Accelerates Expansion into the Middle East Cybersecurity Market from Dubai
Cybersecurity corporation ‘Penta Security’ is actively accelerating its entry into the Middle East […]
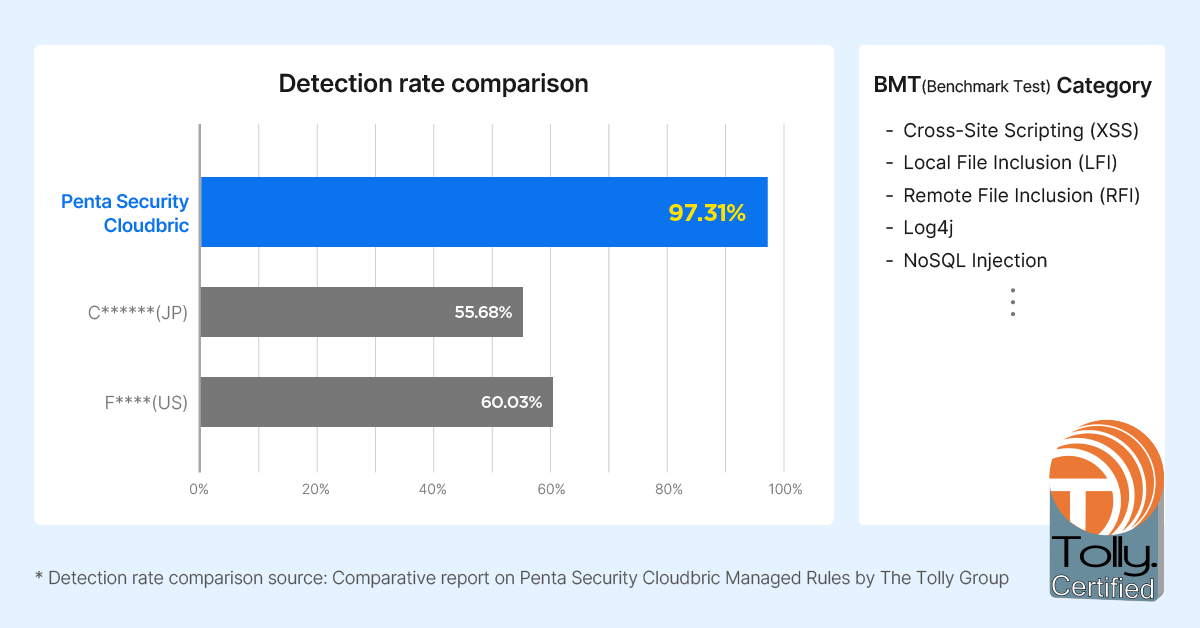
Read morePenta Security’s Cloudbric Managed Rules – API Protection Validated for Top-Tier Performance
Cloudbric Managed Rules – API Protection-Tolly Report Penta Security, a leading cyber security […]
Read more