Enterprise Key Management
Secure storage and management
An Enterprise Key Management product, by definition, takes the encryption keys used for encryption and securely stores and manages them in a separate device. If keys are stored locally within the same server as the encrypted data, in the event of a data breach, hackers would have access to the data and also be able to decrypt it. If the keys are mishandled or lost, then it would be the same as if the data were lost as well.
Database encryption and external key integration
Our D.AMO SG-KMS (Key Management System) handles the entire key lifecycle from generation to destruction in a separate hardware appliance. It can also be integrated to manage external keys as well. This includes encryption keys used across several different enterprise DBMS platforms such as Oracle, SQL Server, and DB2 as well as open-source DBMS such as MariaDB and PostgreSQL.
* Handles all types of keys including symmetric keys, asymmetric key pairs, certificates, etc.
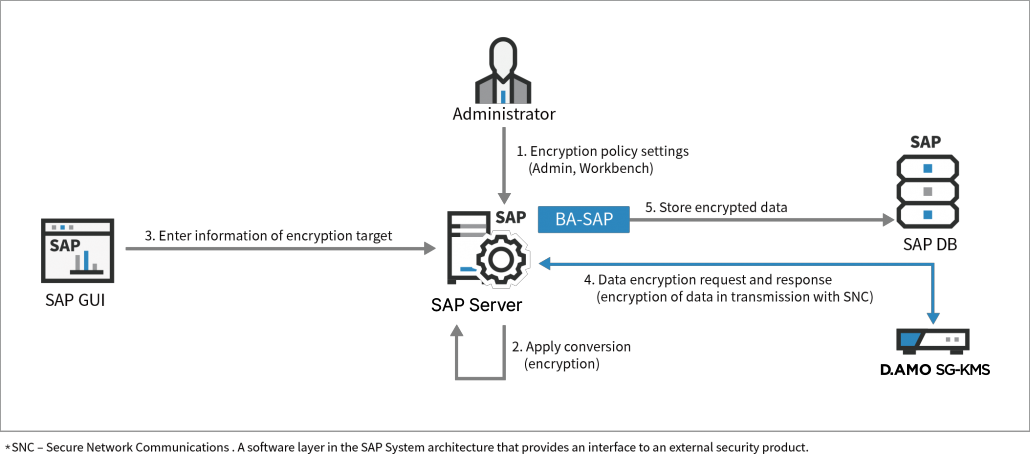
SAP (ERP) Encryption Solution
SAP’s ERP (Enterprise Resource Planning) business-critical application is used by many enterprises across a variety of different industries to handle their corporate data. ERP eliminates data silos and integrates all information used by the different departments and applications into one comprehensive system. Having an entire company’s resources located in one central area can be a lucrative target for hackers. Therefore, ERP demands robust security to protect those company assets.
D.AMO for SAP
Penta Security recognized these risks and developed D.AMO for SAP, a security solution specifically designed for SAP’s ERP. D.AMO for SAP handles the cryptographic transactions and manages all aspects of the key lifecycle for data within the SAP environment. D.AMO for SAP also has an additional feature to prevent changes to field size and data type.
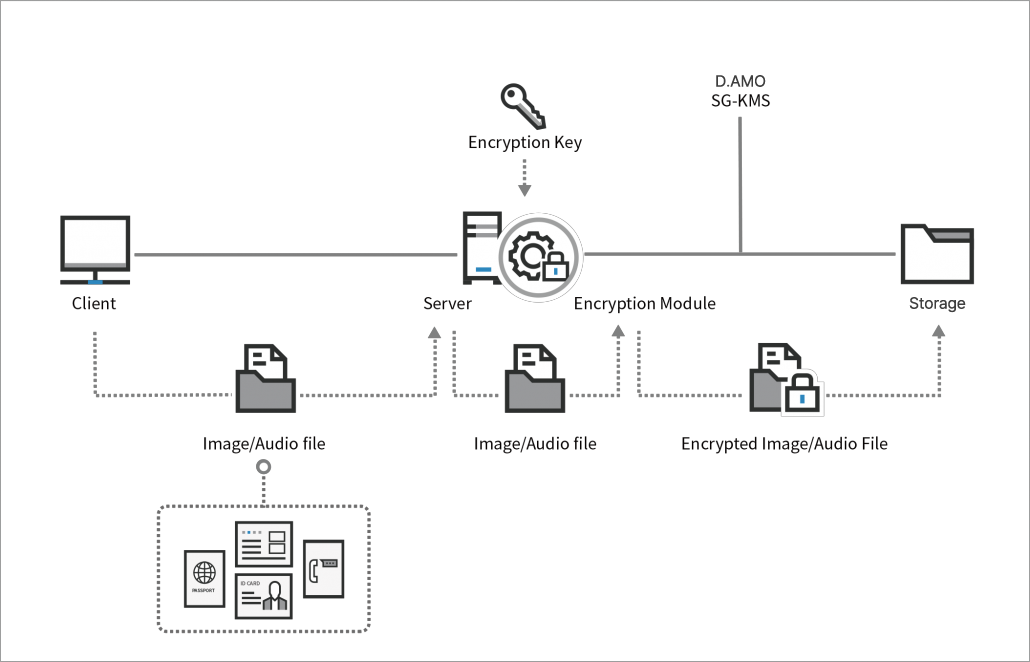
Encryption for Unstructured Data
Unstructured data includes images, audio files, video files, and other unique data types. This data can contain personal information or sensitive corporate data that also requires protection. Encryption and the corresponding key management can be performed for these unstructured data types as well.
Payment Endpoint Key Management
The financial sector is constantly targeted by hackers. One of the common access points hackers attack are payment endpoints such as CAT (consumer activated transaction) applications, POS (point-of-sale) terminals, and ATMs (automatic teller machines). Our enterprise key management solution, D.AMO KMS, can manage all the keys used in encrypting financial data including credit card numbers and account information.
IoT Infrastructure Key Management
Just like any other network infrastructure, the IoT infrastructure has its security risks regarding data. There will soon be a point even in this setting where it will be a standard requirement for data to be encrypted. Because IoT endpoints will be numerous, authentication will play a vital role.
Real life examples where authentication of IoT endpoints is necessary will be in smart metering, heavy machinery, and factory automated equipment. Authentication is based entirely on the encryption keys. The IoT data as well as the IoT endpoint authentication will require the proper management for the lifecycle of all these various types of keys.