Database Encryption
Basic principles and concepts of encryption technology
What is Encryption?
An encryption algorithm changes information into incomprehensible characters through a mathematical process. While other security tools protect a system from intrusion or attack, encryption is a fundamental form of defense that deals with security of the data itself. This means that even in the event of a system breach, compromised data is still only readable by authorized users in possession of the right encryption keys.
Classical Ciphers
A cipher is an algorithm to encrypt and decrypt – it conceals the content of a message or the cryptographic algorithm from unintended recipients. Cryptographic operations have two properties, Confusion and Diffusion:
Confusion makes it difficult to know the content of a message text.
Diffusion makes it difficult to know the pattern of the encryption algorithm.
An effective cipher contains both confusion and diffusion.
Classical ciphers are often divided into transposition ciphers and substitution ciphers.
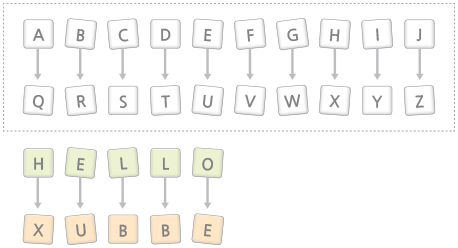
Substitution Ciphers replace the letters throughout the message with other letters.
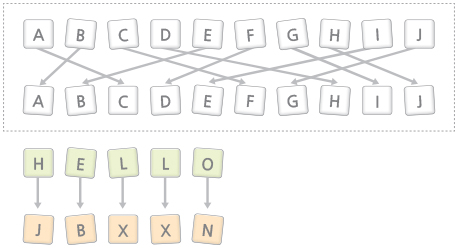
Transposition Ciphers keep the letters themselves unchanged, but their order within the message is scrambled according to a well-defined scheme.
The substitution cipher satisfies the confusion characteristics that make inference of the message difficult. The transposition cipher satisfies the diffusion characteristics that make inference of the encryption algorithm difficult.
Therefore, by applying substitution and transposition in tandem, both confusion and diffusion properties can be simultaneously present.
However, there is a limitation of classical ciphers. If the algorithm is discovered, then the message is easily discovered. And with the invention of the computer, computation capability has rapidly improved thus rendering classical ciphers useless.
The Encryption Key
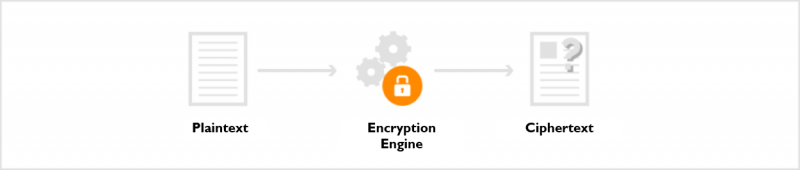
Therefore, the core of current encryption technologies is the ‘encryption key,’ a parameter that specifies the transformation from plaintext (data given before encryption) to ciphertext (a cryptogram, or encrypted data), and vice versa.
Operation of a key is based on the ‘exclusive OR’ operation in mathematical logic. The output of a bitwise exclusive OR operation is the result of an addition and subtraction calculation of each bit of a binary number. The bitwise exclusive OR gives an output of 1 whenever each bit input does not match. Therefore, it becomes the original value by repeating the operation. In other words,
If the plaintext P is operated with the key value K a cryptogram P + K is created.
If this cryptogram is again operated with the key value K, then
(P + K) + K = P
… it can be decrypted to the original plaintext P.
While a simple concept, there are standards for key specifications, such as the length of the encryption key and the number of times the key can be reused. Current standards are only considered safe until the introduction of completely new computing methods such as quantum computation. Therefore proper encryption key management requires a good understanding of various key types and their properties, to securely store, protect and retrieve keys with different specifications.
There are different types of encryption: one-way (also called “hashing”), symmetric, and asymmetric.
One Way (Hashing)
Passwords used for identification use the One-way Encryption algorithm. For example, before saving a password, the password is encrypted. And when a password is ‘password,’ it is encrypted and saved as ‘WaBauZ2.Hnt2.’ There should be no similarity between the plaintext ‘password’ and the cryptogram ‘WaBauZ2.Hnt2.’
The one-way encryption cannot be reversed to convert a cryptogram into plaintext. Passwords encrypted by hashing are not decrypted for verification. Instead, the same hash is performed on a password input and compared against the hashed password stored in the system to verify an ID. This way, the sensitive password need not be stored in plaintext form.
Symmetric Key Encryption
For this method, the encryption and decryption keys are the same. Sometimes referred to as private key encryption, both sender and recipient must have the same symmetric key to receive proper and secure communication.
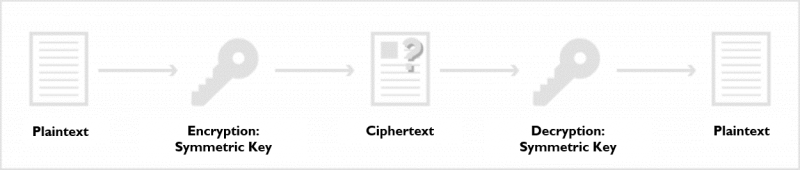
A cryptogram is computed by transforming the plaintext using the binary encryption key value. The recipient of the cryptogram then utilizes the identical encryption key value in the reverse cryptographic algorithm to decrypt the cryptogram. Therefore, the sender and the recipient must securely share knowledge of an identical encryption key. When a person sends an encrypted message to another person, the recipient should also receive the key.
Asymmetric Key Encryption
Asymmetric, or public key, encryption is different from symmetric key encryption because it uses two different keys: a private key and a public key. It encrypts with a public key and decrypts with a private key.
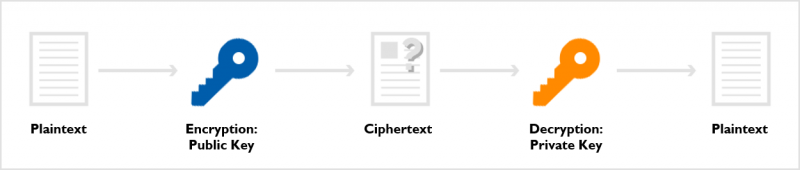
Just as its name implies, a public key is an open key, and anyone can encrypt the plaintext. However, only the person who has a private key can decrypt the ciphertext.
When the locations of a private key and public key are switched, it becomes an ‘e-signature.’
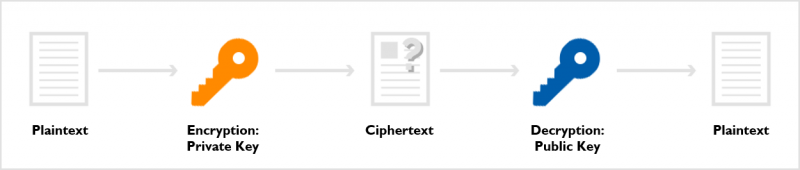
The encryption method is determined based on the environment.
According to different encryption needs, methods and formats are selected. The encryption process is then designed, and the system is implemented. From simple to complex implementations of encryption, selecting an appropriate system depends on one’s security needs and other economic considerations. Simply implementing public keys into an existing private key system does not upgrade it into a public key system. These two key methods are distinct, and a decision between the two has to be made based on need.
For example,
- The private key method (symmetric) is preferred if there is a secure channel of communication for key distribution and management, and if encryption needs to be executed at high speeds.
- The public key method (asymmetric) is preferred if there is no secure channel of communication for key distribution and management, and if transfer non-repudiation is required.
Designing an encryption system is therefore about understanding an environment’s specific requirements so as to select the most appropriate encryption methods.
How to: Database Encryption
While the study of encryption is about trying to explain encryption logic systematically through generalizations and propositions, encryption technology is, based on encryption theories, a product of necessity aimed at creating the most cost-efficient, profitable outcomes in line with economic principles. It is the outcome of a process of transforming, refining, and amalgamating theories for practical application.
According to business requirements, the location for encryption implementation and the characteristics of data can differ. This is why encryption technology needs to be qualified by its business value. Delving into encryption technology, therefore, requires a broad, overall understanding of systems and businesses. This is a recent example of a mobile messenger application encryption system that was designed and implemented. At the most basic level, data encryption was needed in the DBMS (Database Management System), which saves conversations communicated through a messenger.
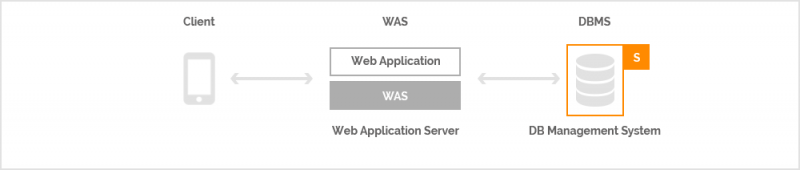
However, in light of general trends in security breaches, the above configuration is incapable of providing sufficient security. In reality, web application encryption needed to be implemented as follows:
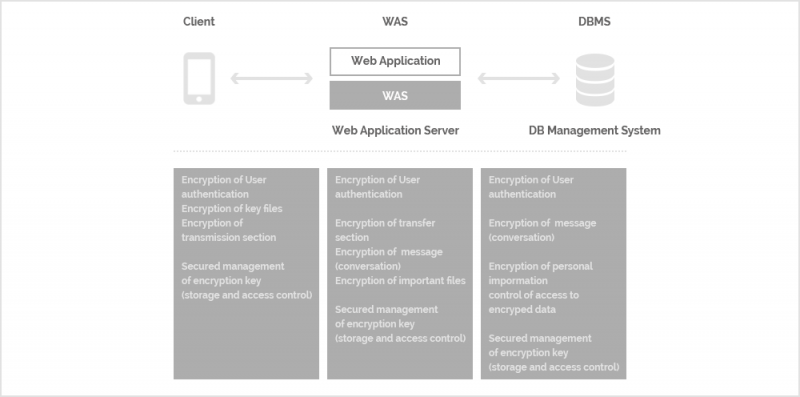
The configuration includes the encryption of user authentication, section encryption, message encryption, file encryption and key management.
All kinds of security system configurations follow secure IT system design principles. Therefore, to perfectly deploy encryption technology, all layers and areas of a system needed to be considered.
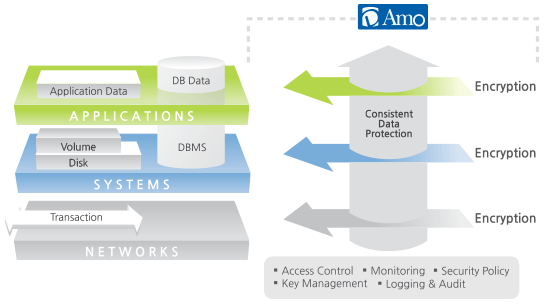
Encryption should be appropriately implemented in all three layers of the IT system, namely the application, system, and network layers. With secure key management, privilege management, and access control, solid encryption is achievable.
Many companies or organizations are hesitant to implement encryption because of the belief that utilizing encryption technology slows down the system’s performance. Even for companies that do implement encryption, they believe that a performance downgrade is simply a necessary trade-off – a price that must be paid in order for their data to be secure.
However, encryption specialists should be able to help implement a system that provides security at the same level for various environments and minimize degradation of system performance. In most cases, the degradation isn’t caused by issues of technology – it is caused by insufficient understanding of the system and poorly designed applications.
In general, most security breaches occur due to poor security administration because unrealistic expectations of a security tool’s capabilities leave a user off-guard. The only way to prevent such incidents is to improve security consciousness across the user group. Until people gain a sufficient understanding of security and receive training in security governance, can proper security administration take place.
Many security vendors may tout the following:
“If you purchase this encryption appliance, all your security concerns will be resolved.”
But this is undoubtedly the wrong attitude: a specialized encryption vendor will always the first talk about the need for security governance and improving the security consciousness across an organization.
Akin to culture, encryption impacts all aspects of a business, including design, development, and operations. Alongside the advancement of the knowledge and information society, data protection is growing in importance. Among various measures for protecting data, from the technical reliability standpoint, the most important and fundamental method is through encryption.
Types of Encryption Targets
Database encryption methods can be differentiated based on their encryption targets.
In file-level encryption, individual database files are encrypted as a whole to restrict unauthorized access. However, partial encryption of the database can be performed with more specific targets as follows:
Cell-level encryption: Individual cells are encrypted separately, with their own unique keys
Column-level encryption: Individual columns of data are encrypted separately, with each column having the same key for accessing, reading, and writing data within the column
Row-level encryption: Individual rows of data are encrypted separately, with their own unique keys for their cells
Table space-level encryption: Individual tablespaces are encrypted as a whole. Each tablespace has a unique key for all of its contents.
By allowing selective encryption of data, such as only encrypting sensitive data, performance is greatly boosted compared to encryption of the entire database file. Among these various methods of partial encryption, column-level encryption provides unique benefits by making certain functionalities possible.
Index searching
With file-level encryption, data has to be fully decrypted to perform a full-text search. However, if index-column encryption is possible, index searching can be performed with the portion of the data that is left unencrypted. This allows search functions to be executed more efficiently.
Encryption of active data
Column level encryption is possible even with data that is “in transit” or “in use,” which is otherwise known as active data. This is especially important for databases that are constantly being accessed or updated.
Database-level access control
Security administrators are able to delegate encryption/decryption keys only to authorized users, to restrict which columns of data users are able to access. Unlike file-level encryption where only OS-level access control can be set up, column-level encryption allows users to enjoy unconstrained access to insensitive data which does not need to be encrypted.
Data Environment and Layer Structure of an IT System
To analyze the data environment, the IT system layer structure should be understood according to the data processing method. The IT system can be conceptualized as being structured according to the following virtual layers:
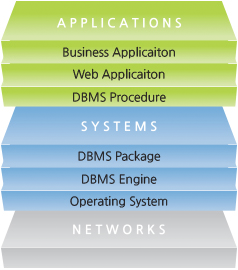
Network: transmits data between servers or between a server and a user device
Operating System: drives the servers or devices, and physically stores data files
DBMS Engine: a core feature of a database system that stores or retrieves data within the database
DBMS Package: provides interworking to process data in the DB server or to externally use the DB server externally
DBMS Procedure: configures applications that use the DB as data storage by interworking with the DB server
Web Application: provides contents to users via the web by interworking with the DB server
Business Application: a large information system that bundles small applications to create large application systems
Data Encryption at the Network Layer
At the Network Layer, the server and the client are interconnected for data transfer. This includes communication between an application server and a DB server, between a networked storage device and a server, and between a server and a terminal. An attacker can collect and steal the transferred data by tapping the communication channel. At this time, to protect data, the data transferred is encrypted in the following way:
Encrypting the communication channel between sender and recipient
By encrypting all data, the efficiency may be lowered; however, because the transmission of data itself can be hidden, this method is highly secure.
Selectively encrypting only specific data among all data transferred
This improves performance by encrypting only the desired information. It requires selective encryption technology.
Encryption at the network layer can physically provide secure encryption between a sender and a recipient. Encryption keys must be generated and managed in a secure manner between a sender and a recipient for secure encryption.
Data Encryption at the Operating System
All data is saved in file format within the computer. Encryption at the OS layer means adding an encryption stage to the file-saving process of the OS.
Encryption function built into the storage device
Storage devices like HDDs encrypt and decrypt data themselves. All saved files are encrypted.
Encryption and decryption by the file system
The OS file system encrypts and decrypts data. All saved files are encrypted.
Encrypt and save only certain files
Files are selectively encrypted and managed. Encryption can also be performed on directories or folders as a whole.
When encryption is carried out at the OS layer, there is no need to implement encryption processing for a database or an application. Therefore, no complex modifications or changes in the existing system are required. However, most OS-level encryption products store encryption keys in user devices or servers, making it difficult to manage access control or set granular security policies.
Data Encryption at the DBMS Engine Layer
The DBMS Engine is a core module that manages input/output and data storage in the DB server. Most DBMS products offer built-in encryption features.
The same operation is performed before and after encryption is applied, whenever information is stored or read in the database. Therefore modifications to existing applications are not required for encryption at this layer, just as with encryption within the OS layer. This unique form of encryption can be described as being transparent to applications and is called Transparent Data Encryption (TDE).
However, most TDE-type encryption products store the decrypted data in the memory, which creates a risk of information leakage. With key management best practices in mind, having both encryption keys and data stored in the same repository would make achieving complete security impossible.
Therefore, key management and the in-memory processing of decrypted data need to be considered carefully before implementing any DBMS Engine-level encryption products.
Data Encryption at the DBMS Package Layer
At the DBMS Package layer, external requests are received and instructions are given for processing by the engine. Encryption at this layer has the advantage that applications at higher layers need not be modified. Because the DBMS engine receives and processes data that has already been encrypted, there is also no security threat to worry about within the memory.
When performing encryption at this layer, you can optionally specify a database table for encryption, and this has excellent performance benefits. In the past, data stored in the database itself is encrypted and therefore there was an absence of a search index functionality. However, encryption vendors nowadays are able to provide index generation functionality that allows for the quick retrieval of encrypted data.
Products for encryption at the DBMS Package level can burden the database server, due to the encryption and decryption that happens whenever data is processed. As such, for practical deployment of such encryption products, it is necessary to provide a means with which to minimize load on the database server.
Data Encryption at the DBMS Procedure Layer
The software in the DBMS Procedure Layer utilize the DBMS API externally.
A separate API that supports encryption when communicating with the database server is necessary for handling encryption at this layer. If the application and the database server reside in different systems, additional encryption at the network layer may be applied.
By calling the encryption API instead of the DBMS API, all the advantages that come with encryption at the DBMS Package layer can be enjoyed, and additionally, the computational burden of encryption and decryption does not get transferred to the database server. Furthermore, it addresses security threats that occur in the network section within the network environment. However, this requires a certain level of application modification.
Data Encryption at the Web Application Layer
The system configuration of many online information services in recent years is becoming increasingly complex.
Its multi-tier configuration consists of a web server, a web application server, and a database server. The web application server links the web server and the database server as well as controls data flow.
Since the function of connecting to the database server is similar to the function performed by the DBMS Procedure application, only the location where encryption takes place differs. The method of encryption at the Web Application layer is the same as in the DBMS Procedure layer and therefore both share the same advantages and disadvantages.
Data Encryption at the Business Application Layer
Business applications are often large systems that integrate applications.
Even when a DBMS is deployed for internal data management, it is included as a separate system for managing storage. Therefore, it is impossible for developers of business applications to call or use a DBMS directly. The storage management subsystem should be modified, or a secondary subsystem should be added, in order to encrypt the Business Application layer.
As business applications are implemented based on independent design and implementation principles, adding and modifying new subsystems is costly and labor-intensive.
Encryption methods, along with their pros and cons, are the same for this layer as in the DBMS Procedure and Web Application layers.
Comparison of Encryption Methods
Please refer to the table below to help determine the appropriate data protection encryption technology.
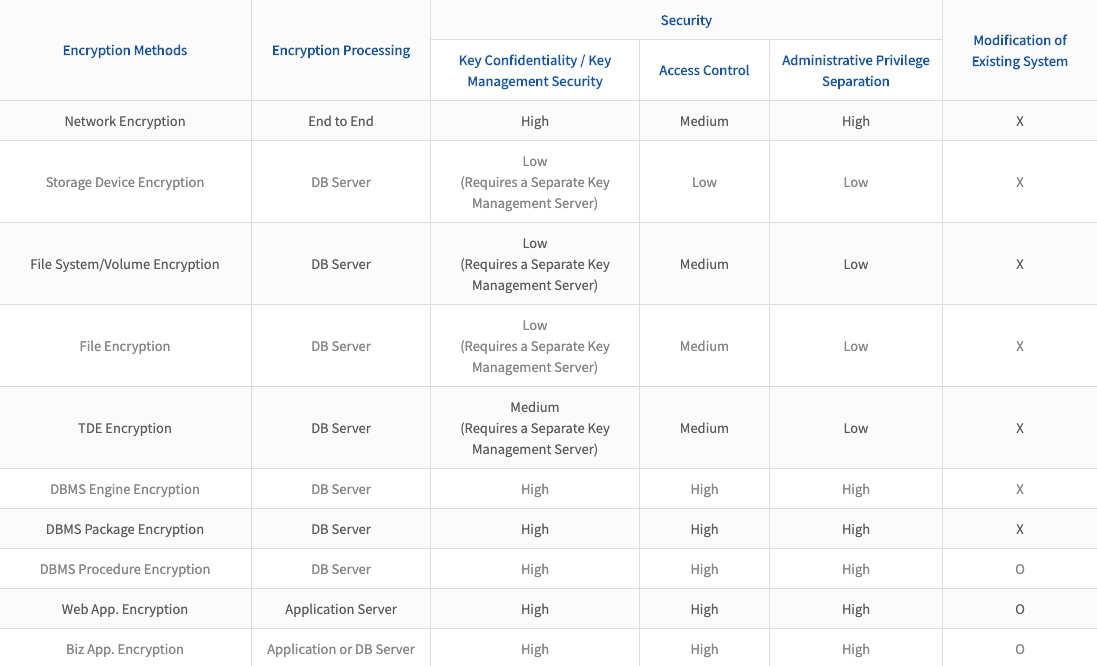
With a thorough understanding of the entire ICT system and business environment, technology can be deployed to satisfy both security and performance needs. As a specialized encryption vendor, Penta Security provides all the encryption technologies necessary for data protection.