Infographic: Security Trends and Risks in the 2nd Quarter of 2020
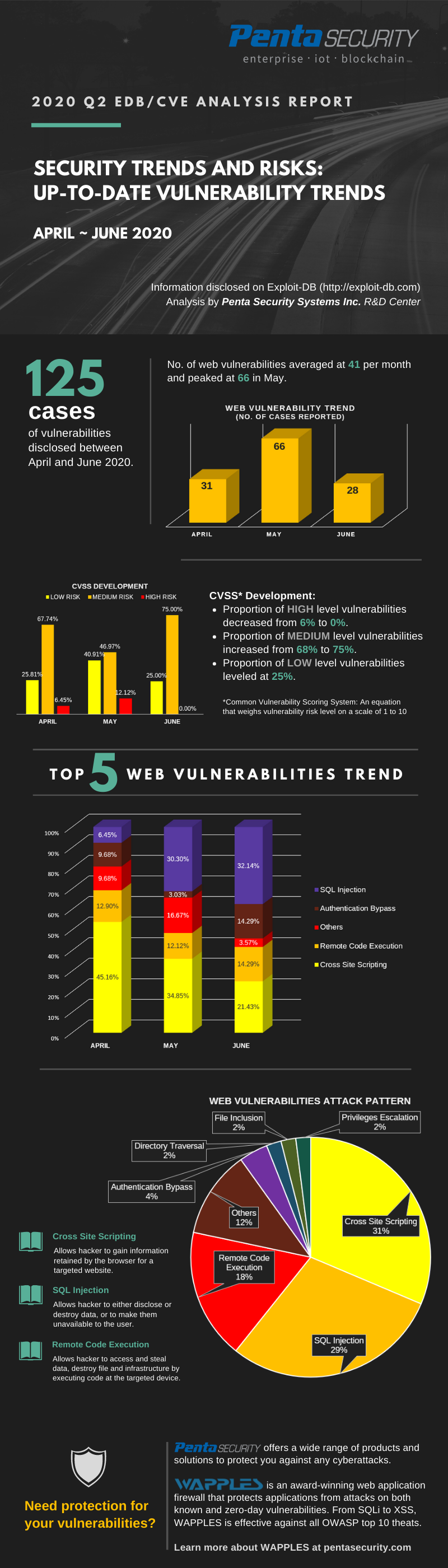
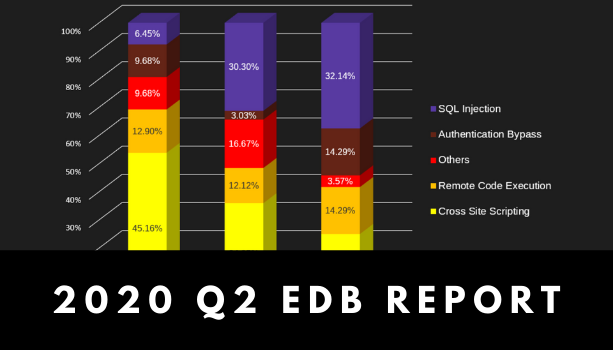
In the 2nd quarter of 2020, there was a significant increase in the number and proportion of low-risk vulnerabilities compared to the first quarter.
Take a look at this infographic for more details on the latest web vulnerability trends and keep yourself prepared with WAPPLES!