How to Prevent Business Hacking? 6 Things to Check Before Adopting Encryption
Penta Security’s encryption platform D.AMO was recently featured in Korea’s leading IT magazine, Yozm IT.
With data breaches continuously making headlines, cybersecurity threats are no longer confined to a handful of large corporations. Today, from small startups to multinational enterprises, every organization that stores data is a potential target. Among the many defense strategies available, encryption stands out as one of the most reliable ways to ensure that even if data is stolen, the stolen information remains unreadable and unusable.
Together, Penta Security and Yozm IT explored the real purpose of hackers, why encryption is essential, the most critical considerations for adoption, whether enterprises really need dedicated solutions, and which factors IT managers should review before implementation.
Click here to read the article (in Korean)
Why Do Hackers Attack?
Hackers are not pranksters simply breaking into systems for fun. Every attack has a clear motive. Some aim to paralyze services and demand ransom, while others steal sensitive corporate data to sell or use for extortion. Ultimately, hackers pursue two goals: disrupt services or steal data to cause irreversible damage.
Service Disruption
Some hackers attack to halt the normal operation of an organization’s services, often seeking monetary gain. Security solutions like web firewalls usually mitigate these incidents, and organizations can restore services within days, keeping overall damage relatively limited.
Data Theft
Far more dangerous is the theft of critical corporate data. Unlike temporary disruptions, stolen data cannot be deleted or recovered once exposed. Moreover, it rarely remains in the hacker’s possession alone, often spreading through multiple channels and leading to secondary damages.
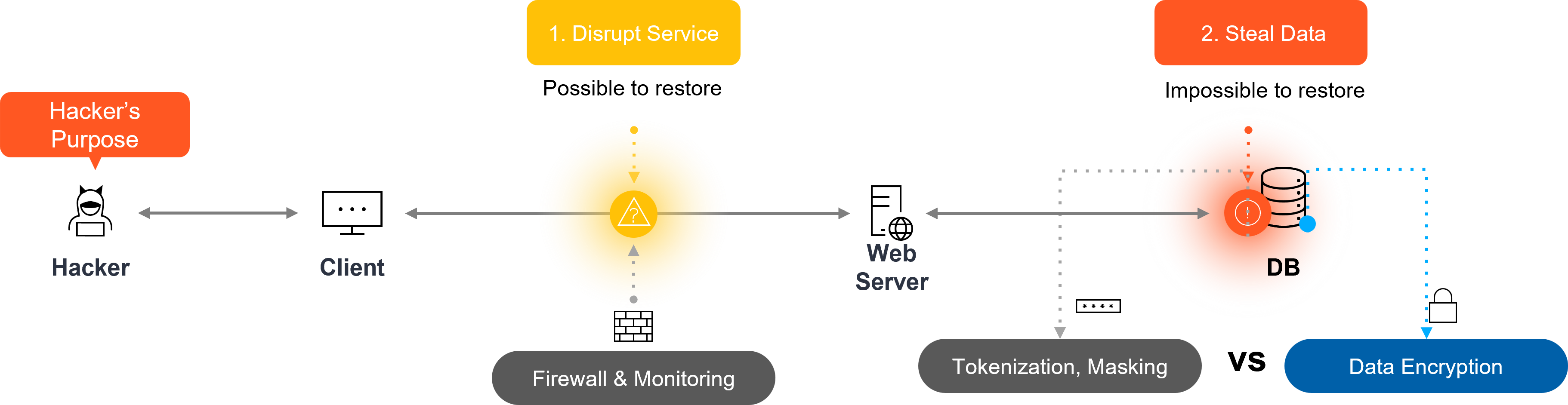
Since the primary aim of hackers is to disrupt services or steal data, the only effective countermeasure is clear: protecting data in advance.
Why Encryption Matters
Governments and regulatory bodies worldwide have established numerous rules to combat cyberattacks. However, hacking techniques evolve constantly, and damages continue to escalate, costing businesses trillions of dollars globally each year.
Although organizations adopt solutions like DRM (Digital Rights Management), DLP (Data Loss Prevention), or VDI (Virtual Desktop Infrastructure), many face challenges with cost, resource management, and limitations in fully eliminating breach risks.
The most fundamental, cost-effective, and reliable method is encryption.
Common Questions About Encryption
Q: Do we really need dedicated encryption solutions?
If encryption is used only for internal documents, in-house solutions may suffice. However, authorities require certified encryption modules for sensitive data such as customer information. Without certified solutions, companies must prove that their self-developed encryption is equally secure, which is practically impossible.
A dedicated encryption solutions with proven key management are essential for organizations seeking ISMS-P certification. ISMS-P evaluates whether protection requirements such as personal data encryption, key management, and algorithm suitability are fully met. Proprietary encryption algorithms typically fail the audit due to lack of verifiable security. Ultimately, encryption should be viewed not as a cost, but as insurance. The financial, legal, and reputational damage from a breach far outweighs preventive investments.
Q: What is the most important factor in encryption?
Performance in real-world environments is often more critical than the technology itself. Many fear that encryption will slow down systems, but proven solutions like Penta Security’s D.AMO are optimized to integrate seamlessly, sometimes even improving performance.
In practice, what matters most is not only the encryption algorithm but also the expertise and experience behind its deployment.
Understanding Encryption
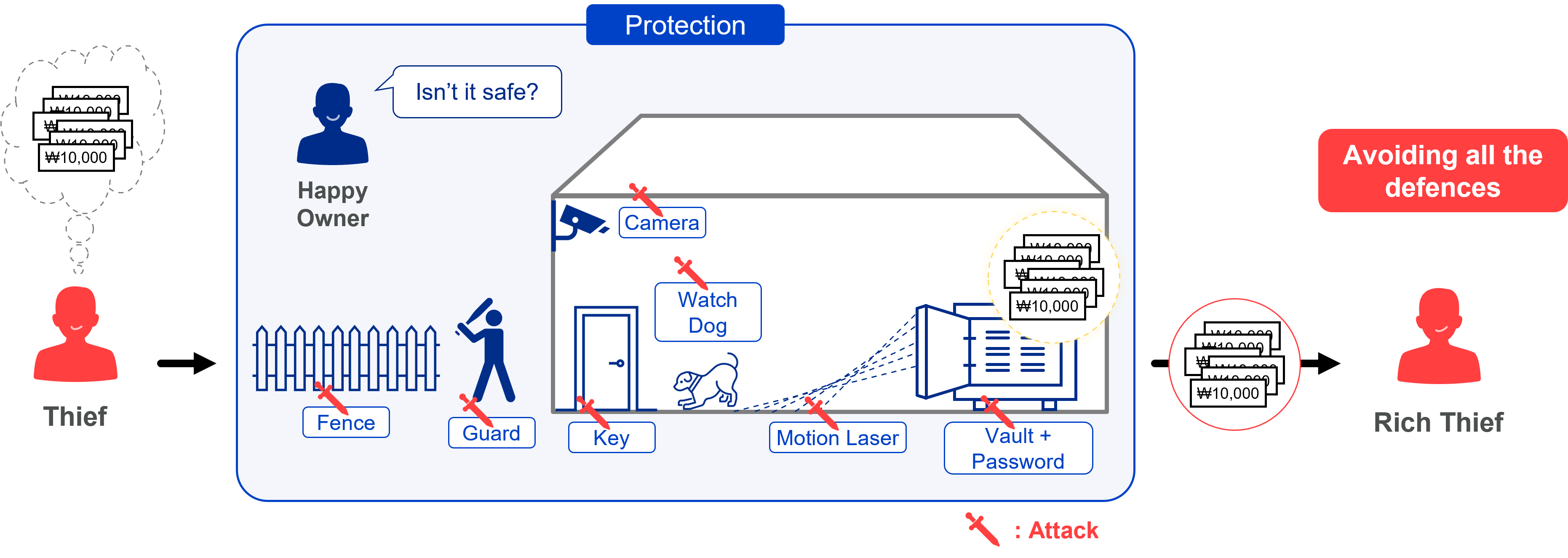
Think of a vault filled with money. You might install CCTV cameras, security guards, and barriers to protect it. But if a thief bypasses them, they can steal the money.
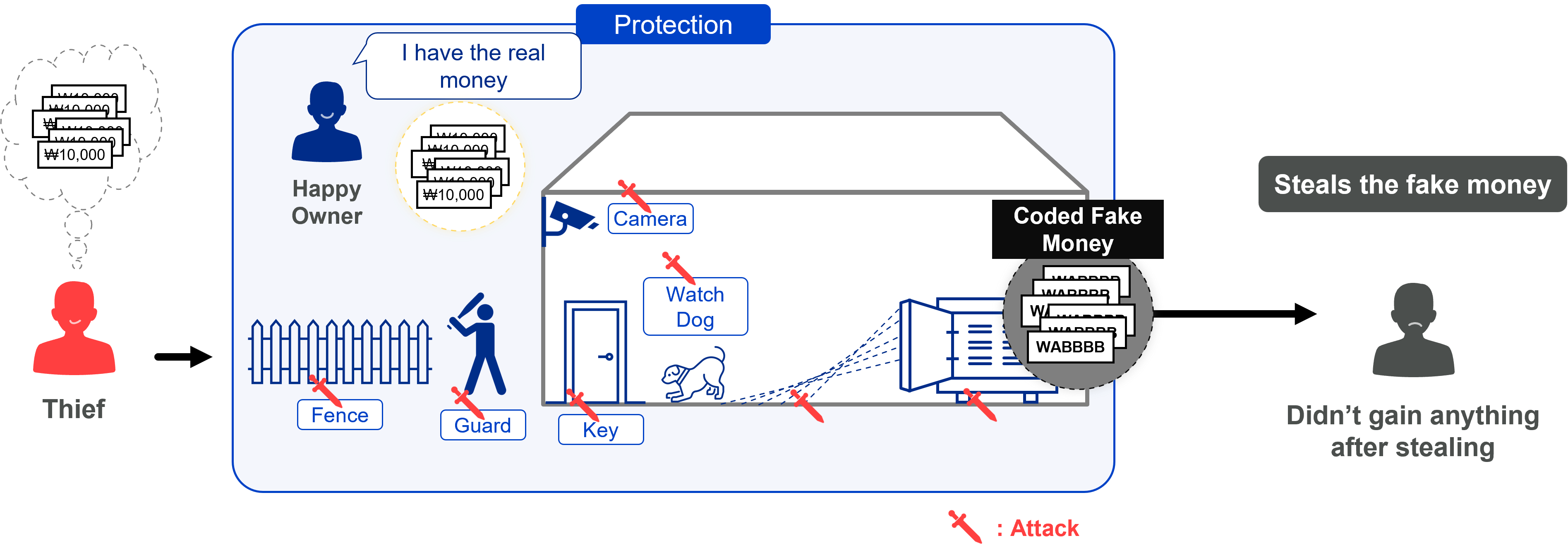
However, if the money inside is encrypted, it becomes useless paper without the right key. Similarly, encrypted data is unreadable even when stolen.
Encryption is the process of transforming plain text into ciphertext through mathematical operations. This ensures that sensitive data remains secure and unusable without the correct key.
6-Point Checklist Before Adopting Encryption
Organizations increasingly recognize the importance of data security, but face challenges when choosing among the many encryption products available. To simplify the decision, here are six key factors to check:
1. Compliance and Certification
Encryption and key management must comply with laws such as data protection acts and healthcare regulations. Check whether the solution has official certifications to ensure full compliance.
2. Compatibility Across Systems and Environments
Modern IT infrastructures are complex, spanning hybrid clouds, IoT, smart factories, and blockchain. Encryption must work across all environments, ideally with centralized monitoring and management capabilities.
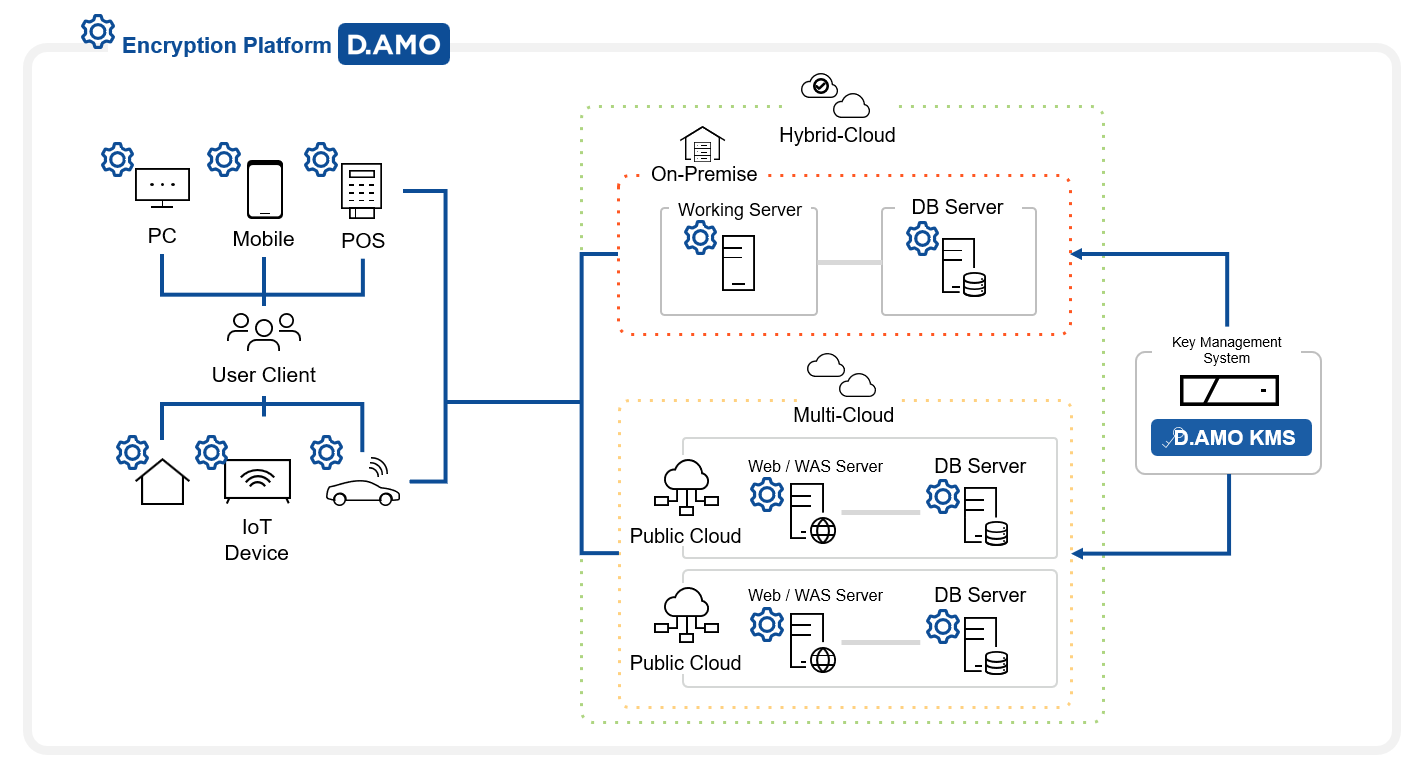
3. Support for Multiple Algorithms
Strong encryption requires support for both global and domestic standard algorithms. Ensure the solution supports international standards as well as local ones like SEED, ARIA, and lightweight algorithms such as LEA and HIGHT.
4. Dedicated Key Management System
Encryption is only as strong as its key management. A dedicated key management appliance ensures secure storage and management without complex installations or risks of exposure.
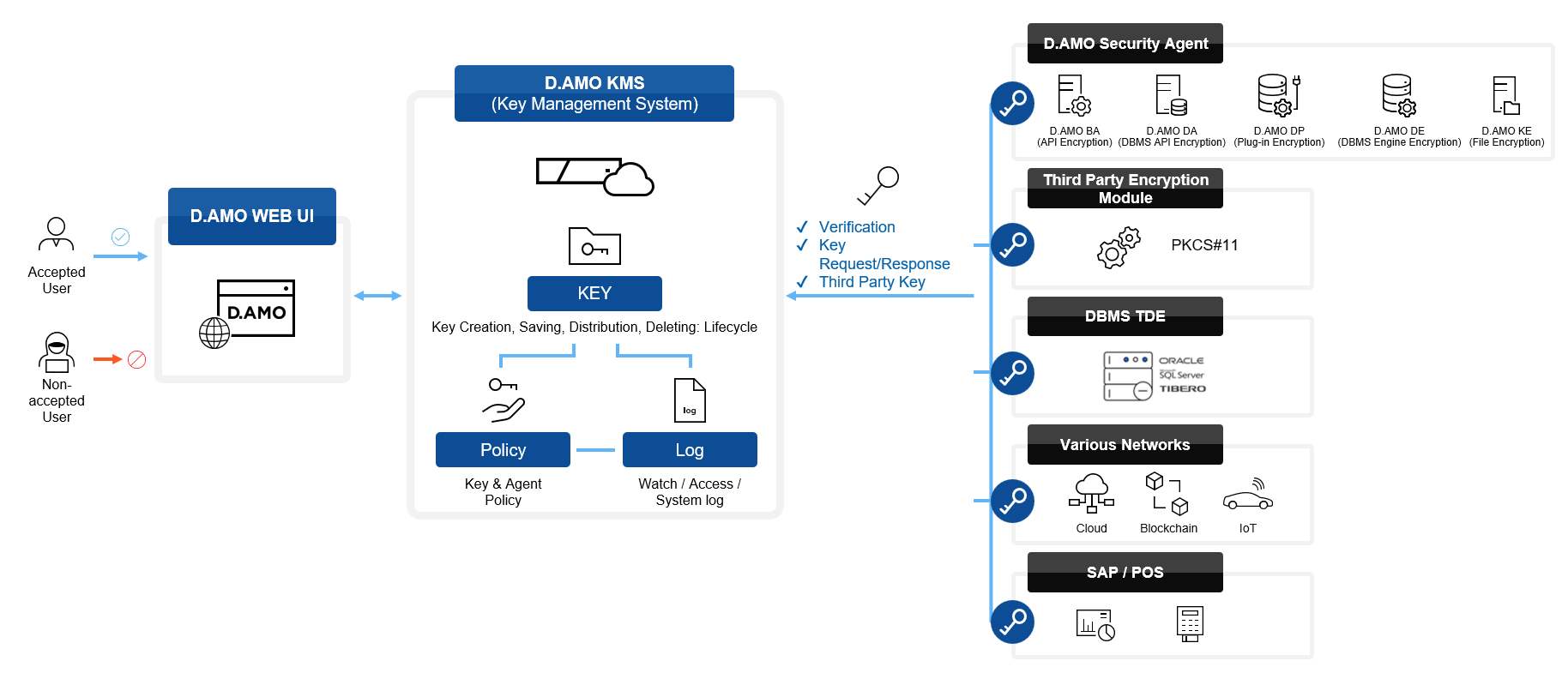
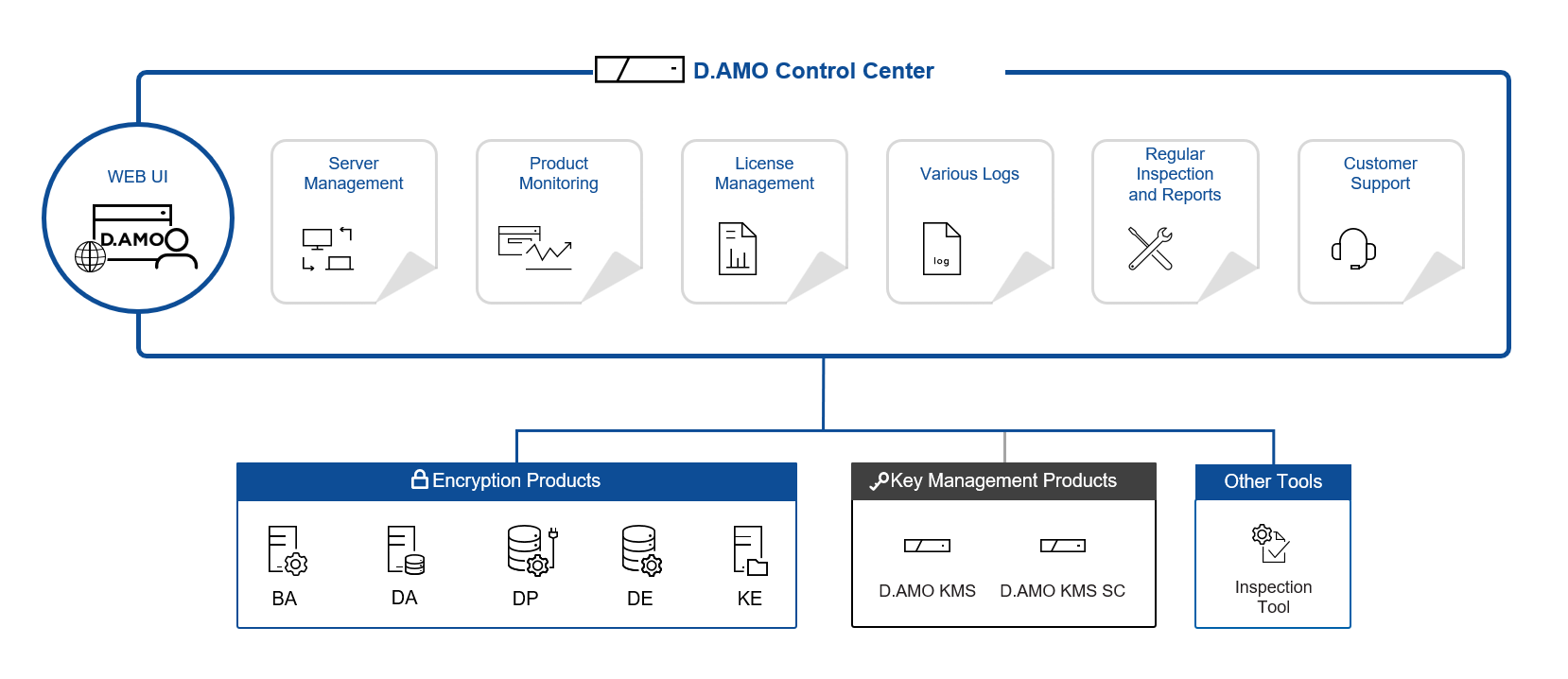
5. Centralized Management System
IBM’s Cost of a Data Breach Report 2021 found that organizations with complex systems paid 52.4% more per breach on average—around USD 2.15 million more. Organizations can reduce risk by using a centralized system for encryption and key management, which provides unified monitoring, configuration, access control, and audit logs.
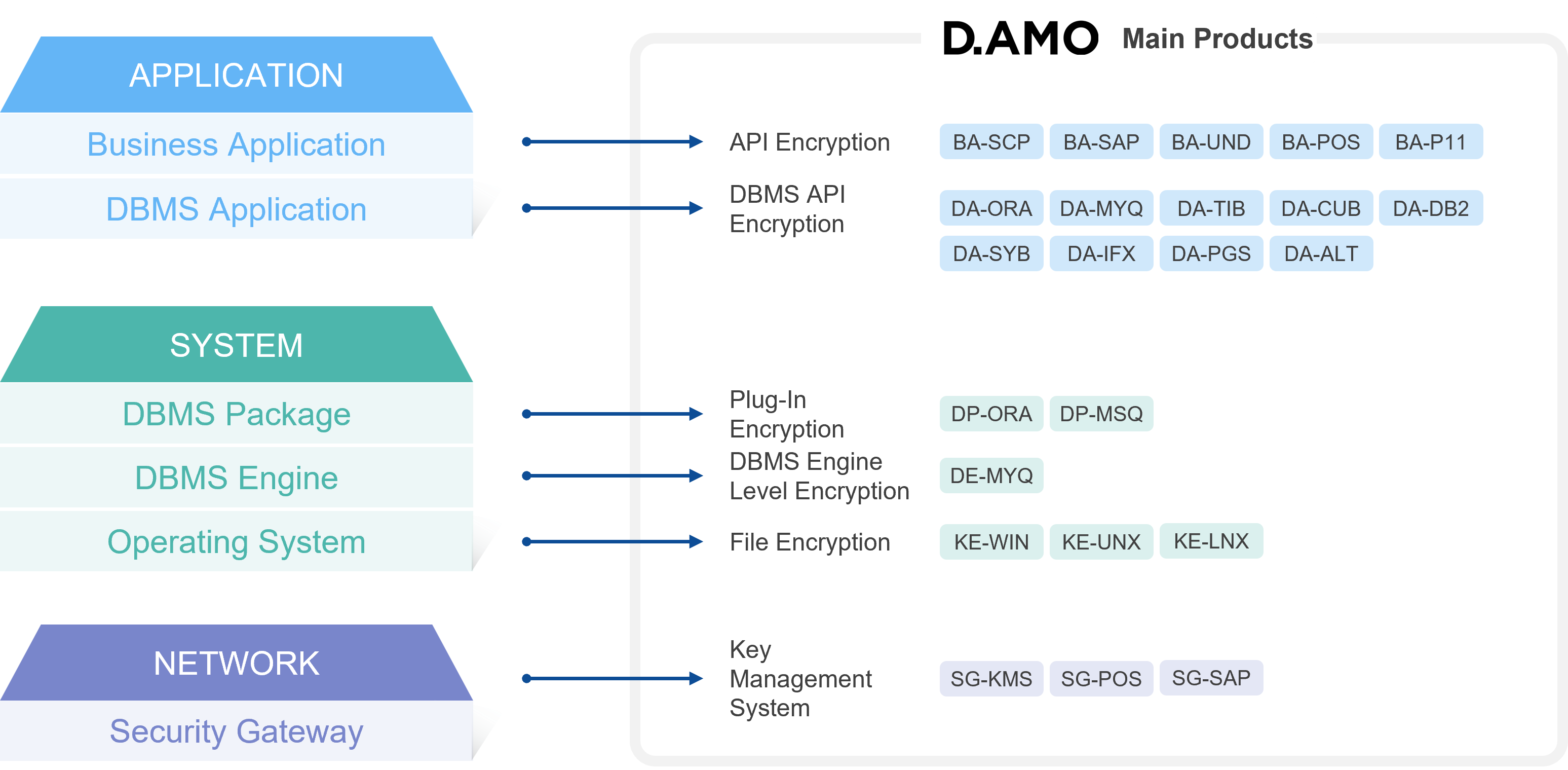
6. Cost Efficiency
Encryption and key management require advanced technologies and can be expensive. Enterprises must evaluate cost efficiency from the start, since replacing solutions after implementation is difficult. Solutions that deliver both high performance and strong security without degradation are ideal.
Data Security is Customer Trust
In conclusion, data equals trust. Encryption, key management, and the six essential considerations outlined above represent more than just technical issues. They represent the foundation for customer trust and long-term business survival.
Instead of being overwhelmed, start small. Use this checklist to evaluate your organization’s current security posture today. That simple step may drive major improvements tomorrow.
Click here to subscribe our Newsletter
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D.AMO
Click here for inquiries regarding the partner system of Penta Security
Check out the product lines of Cloudbric by Penta Security:
Cloud-based Fully Managed WAAP: Cloudbric WAF+
Agent based Zero Trust Network Access Solution: Cloudbric PAS
Agentless Zero Trust Network Access Solution: Cloudbric RAS
Click here for inquiries regarding the partner system of Cloudbric

