[Penta Pedia] What is Cryptographic Decryption
Cryptographic Decryption: The Core of Data Security in the Digital Era
In today’s rapidly advancing information society, data has become the most valuable resource for creating new value. At the same time, security threats targeting sensitive personal information, financial data, and corporate trade secrets are growing at an alarming pace. The most fundamental and indispensable technology to counter these threats is encryption. However, just as important as encryption is the process of cryptographic decryption, which ensures that only authorized users can access and reuse encrypted data when necessary.
Cryptographic decryption goes beyond simply converting ciphertext back into plaintext. Specifically, it has evolved into a critical technology that guarantees data availability, integrity, and trustworthiness. As a top global cybersecurity company, Penta Security continues to strengthen both encryption and decryption technologies to ensure robust global cybersecurity for businesses worldwide.
Principles of Decryption: Symmetric Key vs Asymmetric Key
Decryption technologies can be divided into two main approaches depending on the type of key used: symmetric and asymmetric.
Symmetric Key
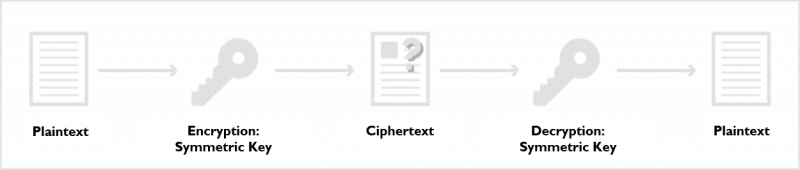
Symmetric key encryption uses the same key for both encryption and decryption. The sender and receiver exchange this shared key, called a secret key or private key.
- Advantages: The algorithm is simple, offering extremely fast processing speed and low computational overhead. This makes it highly efficient for handling large volumes of data.
- Disadvantages: The major weakness lies in secure key distribution. If the key is leaked, all encrypted data can be decrypted, and forged messages can be created. Additionally, as more participants join communication, the number of required keys grows exponentially, making key management highly complex.
Asymmetric Key
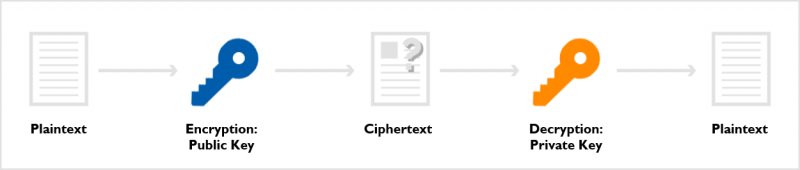
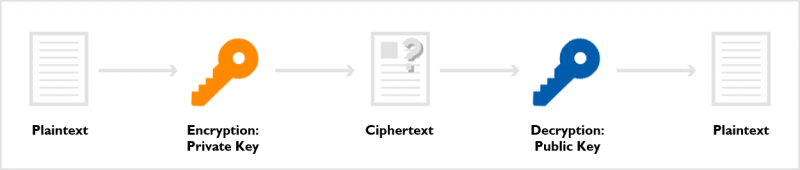
Asymmetric key encryption uses a pair of keys: a public key and a private key. Anyone can freely distribute the public key, while the owner securely keeps the private key. The core principle states that only the corresponding private key can decrypt data encrypted with the public key.
- Advantages: It solves the key distribution problem inherent in symmetric encryption. When you securely obtain the recipient’s public key, you can establish secure communication and manage keys more efficiently because only the private key requires strict protection.
- Disadvantages: Because it relies on complex mathematical computations, it is slower than symmetric encryption and unsuitable for encrypting large datasets.
Modern Encryption Trends: The Hybrid Approach
The latest encryption systems combine the strengths of both symmetric and asymmetric methods in a hybrid approach. This method leverages the fast computation of symmetric encryption along with the secure key exchange of asymmetric encryption.
The most common example is the TLS/SSL handshake in HTTPS communications. During this process, asymmetric keys are used to securely exchange a session key, and then symmetric encryption is applied for actual data transfer. This hybrid design ensures both high speed and robust security.
Decryption vs Cryptanalysis
Although decryption and cryptanalysis both deal with encrypted data, their nature and objectives are fundamentally different.
- Decryption is a legitimate process where authorized users employ valid keys to restore ciphertext into plaintext.
- Cryptanalysis, on the other hand, is an attack method that seeks to uncover plaintext or keys without knowing them, often by exploiting weaknesses in the encryption system.
This distinction is best explained through Kerckhoff’s Principle, which states that the security of an encryption system should depend solely on the secrecy of the key, not on the secrecy of the algorithm. Modern cryptography follows this principle by making algorithms public and subjecting them to extensive expert scrutiny. While decryption restores plaintext through established processes, cryptanalysis attempts to exploit algorithmic weaknesses, posing a very different challenge.
Why Encryption and Decryption Are Essential for Data Protection
Encryption and decryption are not merely technical processes, but strategic pillars of compliance and trust in the digital age. Data goes through its entire lifecycle—from creation, storage, transfer, usage, to disposal—and at every stage, cryptographic protection ensures secure flow and availability.
First, global regulations such as the EU’s GDPR and the US’s HIPAA mandate strict safeguards for sensitive data. Moreover, companies are legally required to implement encryption and controlled decryption systems, ensuring that only authorized users can access protected information. Consequently, non-compliance can result in heavy fines and legal liabilities, which makes encryption and decryption systems a critical investment for businesses.
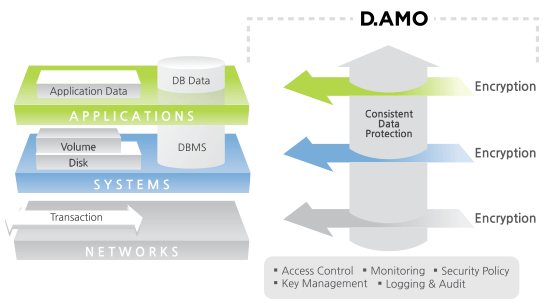
Therefore, solutions like Penta Security’s D.AMO integrated encryption management platform have become essential for enterprises to meet these compliance demands. In particular, its D.AMO KMS (Key Management System) securely manages all encryption and decryption keys, and as a result, enables companies to respond effectively to evolving security threats and regulatory challenges.
Conclusion
Cryptographic decryption is more than a technical necessity; it is a strategic enabler of trust and security in the modern digital world. With Penta Security’s D.AMO platform, enterprises can implement robust encryption and decryption processes across diverse business environments, setting a global standard in database and data protection.
When encryption, decryption, and systematic key management operate seamlessly together, true data protection is achieved.
Click here to subscribe our Newsletter
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D.AMO
Click here for inquiries regarding the partner system of Penta Security
Check out the product lines of Cloudbric by Penta Security:
Cloud-based Fully Managed WAAP: Cloudbric WAF+
Agent based Zero Trust Network Access Solution: Cloudbric PAS
Agentless Zero Trust Network Access Solution: Cloudbric RAS
Click here for inquiries regarding the partner system of Cloudbric