Unstructured Data Encryption: What and How
Structured vs Semi-Structured vs Unstructured Data
Understanding Data Types by Structure
Data can be broadly categorized based on structural characteristics into three types: structured data, semi-structured data, and unstructured data.
Structured data refers to data that adheres to a predefined schema, such as that found in relational databases (RDBs) or spreadsheets. It is organized into clearly defined rows and columns, making it the easiest for computer systems to manage and analyze using standardized query languages like SQL.
Semi-structured data includes formats like XML, HTML, and log files. While it does not reside in fixed fields, it still contains some level of structure through metadata or schemas that guide interpretation.
Unstructured data, on the other hand, represents the broadest category. It lacks a predefined data model or schema, making it more challenging to manage. Yet, this form of data is growing three times faster than structured data in most organizations, complicating storage and security management.

What is Unstructured Data?
In recent years, the data landscape has undergone dramatic changes. As a result, data security paradigms have evolved as well. Traditionally, cybersecurity strategies focused on structured data, such as customer information or financial records stored in relational databases.
However, today’s enterprises primarily handle and utilize unstructured data, data that does not fit into fixed fields. This includes document files, images, videos, voice recordings, messenger conversations, and geolocation data.
While structured data resides in well-organized tables and relational databases, unstructured data is typically stored in non-relational formats. Its growing significance is also linked to its utility in powering artificial intelligence (AI) applications like machine learning (ML) and natural language processing (NLP).
Security Risks of Unstructured Data
As the volume of unstructured data increases, so do the associated security risks, particularly when it contains sensitive personal information. For instance, images of IDs, passports, bankbooks, or audio files containing personal data often exist in unstructured formats.
Global-scale data breaches are no longer hypothetical threats but real challenges, and most conventional security systems—designed primarily for structured data—fall short in addressing the vulnerabilities of unstructured data. As a result, unstructured data encryption has become more than a technical task; it is now a critical factor in ensuring corporate sustainability.
D.AMO: Comprehensive Encryption for Unstructured Data
Penta Security’s D.AMO solution addresses the growing need for robust security across diverse data formats. It is a comprehensive data encryption platform designed for unstructured data encryption in modern IT environments.
Technical Challenges in Encrypting Unstructured Data
Unlike structured data, unstructured data lacks predefined fields, making it difficult to apply column-level encryption. Moreover, because it often consists of large files, traditional encryption and decryption processes can lead to system performance degradation.
D.AMO overcomes these challenges by offering multiple encryption methods optimized for heterogeneous and complex unstructured data environments.
Multi-Layer Encryption: Kernel, Agent, and API-Level Security
D.AMO supports encryption across various layers of enterprise architecture such as kernel-level, agent-level, and API-level, allowing organizations to adopt the most suitable approach for their IT infrastructure.
For example:
- D.AMO KE operates at the OS kernel level, encrypting and decrypting files and folders in real time without requiring any changes to application source code.
- D.AMO BA-SCP installs an API module on the application server, enabling the system to encrypt data before sending queries to the database management system (DBMS).
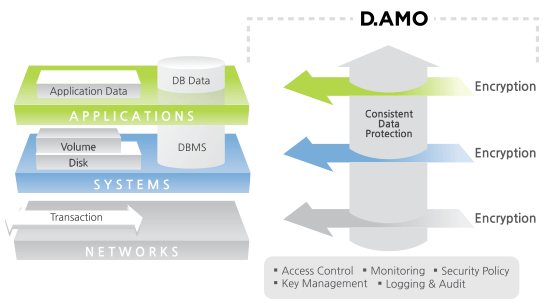
This multi-layered strategy goes beyond offering product variety. It represents a strategic approach to cybersecurity. Since enterprise IT environments vary from legacy systems to new cloud-based platforms and Internet of Things (IoT) devices, a single encryption method cannot adequately protect all use cases.
D.AMO’s layered encryption options empower customers to choose the most effective method for their specific environment. This reduces the typical barriers to encryption deployment, such as the need to modify applications or concerns about performance overhead. Ultimately, it allows enterprises to build and manage a unified protection ecosystem for unstructured data encryption.
Click here to subscribe our Newsletter
Click here for inquiries regarding the partner system of Penta Security
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D.AMO
Check out the product lines of Cloudbric by Penta Security:
Cloud-based Fully Managed WAAP: Cloudbric WAF+
Agent based Zero Trust Network Access Solution: Cloudbric PAS
Agentless Zero Trust Network Access Solution: Cloudbric RAS
Click here for inquiries regarding the partner system of Cloudbric

