[Penta Pedia] InfoStealer: The Rising Malware Threat Targeting Your Data
InfoStealer: The Silent Cyber Threat Lurking in Your Digital Life
In the age of digital convenience, a new and dangerous threat has emerged, the InfoStealer. These malicious programs go far beyond slowing down your computer or displaying annoying pop-ups. Instead, they are sophisticated cyber weapons designed to steal your most valuable data, including personal information and financial credentials.
As one of the most notorious forms of malware in recent years, InfoStealers have gained serious attention within the global cybersecurity industry. Indeed, these stealthy programs secretly collect sensitive data such as login credentials, banking information, cryptocurrency wallets, and even messaging app accounts. The danger escalates when the stolen data becomes a gateway for large-scale ransomware attacks or deeper intrusions into corporate networks.
Unlike early cyber threats that focused on destruction or notoriety, today’s attacks are calculated and profit-driven. With a single successful InfoStealer infection, cybercriminals can harvest dozens or even hundreds of credentials at once, then sell them on the dark web or use them in secondary attacks to gain substantial financial rewards.
This makes InfoStealers not only a personal threat but also a growing risk to organizational security worldwide.
How InfoStealers Infect Without Detection
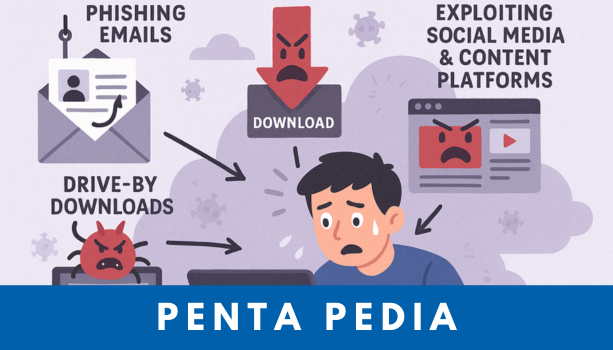
What makes InfoStealers especially dangerous is their ability to infect devices without raising suspicion. In result, threat actors exploit everyday digital behaviors, making it easy for users to fall victim. Here are four most common attack vectors:
-
Phishing Emails
Firstly, phising emails are disguised as delivery updates, bank security alerts, or online sale promotions through email. The moment a user clicks on a malicious link or opens an attachment, the InfoStealer installs itself silently.
-
Fake Downloads
Secondly, arising number of infections originate from users downloading free or cracked software. For example, recent reports illustrate fake websites impersonating popular AI services like ChatGPT and Midjourney have been promoted via Google and YouTube ads leading unsuspecting users straight to InfoStealers.
-
Exploiting Social Media and Content Platforms
Moving on, have you ever seen links shared in YouTube video descriptions or social media posts labeled as “useful tools”? Actually, they are InfoStealer distribution channels. Younger audiences, who frequent these platforms more, are at higher risk.
-
Drive-by Downloads via System Vulnerabilities
Lastly, this is the most dangerous method as cybercriminals can infect users without requiring them to click anything at all. Cybercriminals exploit outdated browsers or unpatched plugins to automatically install malware with InfoStealers, making it nearly impossible to detect the threat until it causes damage.

How to Protect from InfoStealers
Thankfully, defending against InfoStealers is possible with a few essential cybersecurity practices. Both individuals and organizations must stay proactive and vigilant.
- Avoid Suspicious Emails and Links
Never click on links or open attachments from unknown or untrusted sources. Pay special attention to compressed files, documents, or executables. If unsure, verify the sender through a separate channel before interacting.
- Download Only from Official Sources
Always use official websites or trusted app stores to download software. Avoid downloading programs through search engine ads or YouTube links, which are common infection sources.
- Keep Systems and Software Updated
Apply security patches as soon as they’re released. Don’t postpone updates for operating systems, browsers, or plugins. Enabling automatic updates is highly recommended.
- Enable Multi-Factor Authentication (MFA)
Protect important accounts by activating two-factor or multi-factor authentication. Even if cybercriminals steal a password, the additional layer of verification significantly reduces the risk of unauthorized access.
- Regularly Monitor and Manage Your Accounts
Check login activity on your accounts regularly and delete or deactivate accounts you no longer use. Changing your passwords periodically is also a good habit to adopt.
InfoStealers: A Growing Threat to Both Individuals and Enterprises
InfoStealers have evolved beyond basic malware. Today, they directly threaten digital identities and financial assets, serving as critical tools in larger cybercrime campaigns. In other words, cybercriminals increasingly use them as the first stage in ransomware attacks targeting large enterprises.
As Penta Security emphasizes, enhancing cyber awareness is no longer optional. Cyber threats are not a matter of “if” but “when.” Establishing strong daily security habits and maintaining a responsive cybersecurity posture can make all the difference in protecting against this silent, pervasive threat.
Click here to subscribe our Newsletter
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D.AMO
Click here for inquiries regarding the partner system of Penta Security
Check out the product lines of Cloudbric by Penta Security:
Cloud-based Fully Managed WAAP: Cloudbric WAF+
Agent based Zero Trust Network Access Solution: Cloudbric PAS
Agentless Zero Trust Network Access Solution: Cloudbric RAS
Click here for inquiries regarding the partner system of Cloudbric