OWASP Top 10 2025 RC1 Explained
What Is OWASP and Why It Matters for Web Application Security
OWASP, short for the Open Web Application Security Project, is a global nonprofit community of developers, cybersecurity experts, organizations, and academic institutions working together to enhance web application security. As a leading authority in the field, OWASP publishes widely accepted security documents—most notably the OWASP Top 10 and OWASP API Security Top 10. It also develops open-source security tools, guidelines, and educational resources to help organizations mitigate web-based threats.
As a top global cybersecurity company, Penta Security actively follows OWASP standards to align with the evolving needs of global cybersecurity.

What Is the OWASP Top 10?
Among OWASP’s publications, the OWASP Top 10 stands out as the industry standard for web application security. This document provides a prioritized list of the most critical web application security risks, helping developers and cybersecurity professionals focus on the threats that demand immediate attention.
The OWASP Top 10 is updated every three to four years. The most recent finalized version was released in 2021, and the 2025 edition is now available as a Release Candidate (as of November 2025). These updates reflect the ever-changing threat landscape, incorporating new technologies, attack methods, and feedback from the global security community.
OWASP Top 10 for 2025: What’s New?
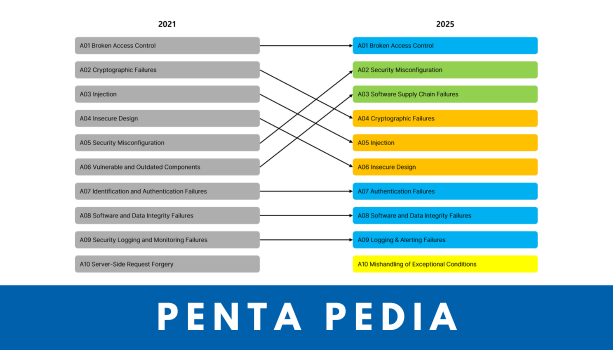
The OWASP Top 10 2025 Release Candidate includes the following security risks:
- A01:2025 – Broken Access Control
- A02:2025 – Security Misconfiguration
- A03:2025 – Software Supply Chain Failures
- A04:2025 – Cryptographic Failures
- A05:2025 – Injection
- A06:2025 – Insecure Design
- A07:2025 – Authentication Failures
- A08:2025 – Software or Data Integrity Failures
- A09:2025 – Logging & Alerting Failures
- A10:2025 – Mishandling of Exceptional Conditions
Compared to the 2021 list, only one brand-new threat category has been added. Most other changes involve broader categories that encompass newly emerging risks, emphasizing a shift in focus from external defenses to internal system design and trust validation.
Comparison: OWASP Top 10 2021 vs. 2025
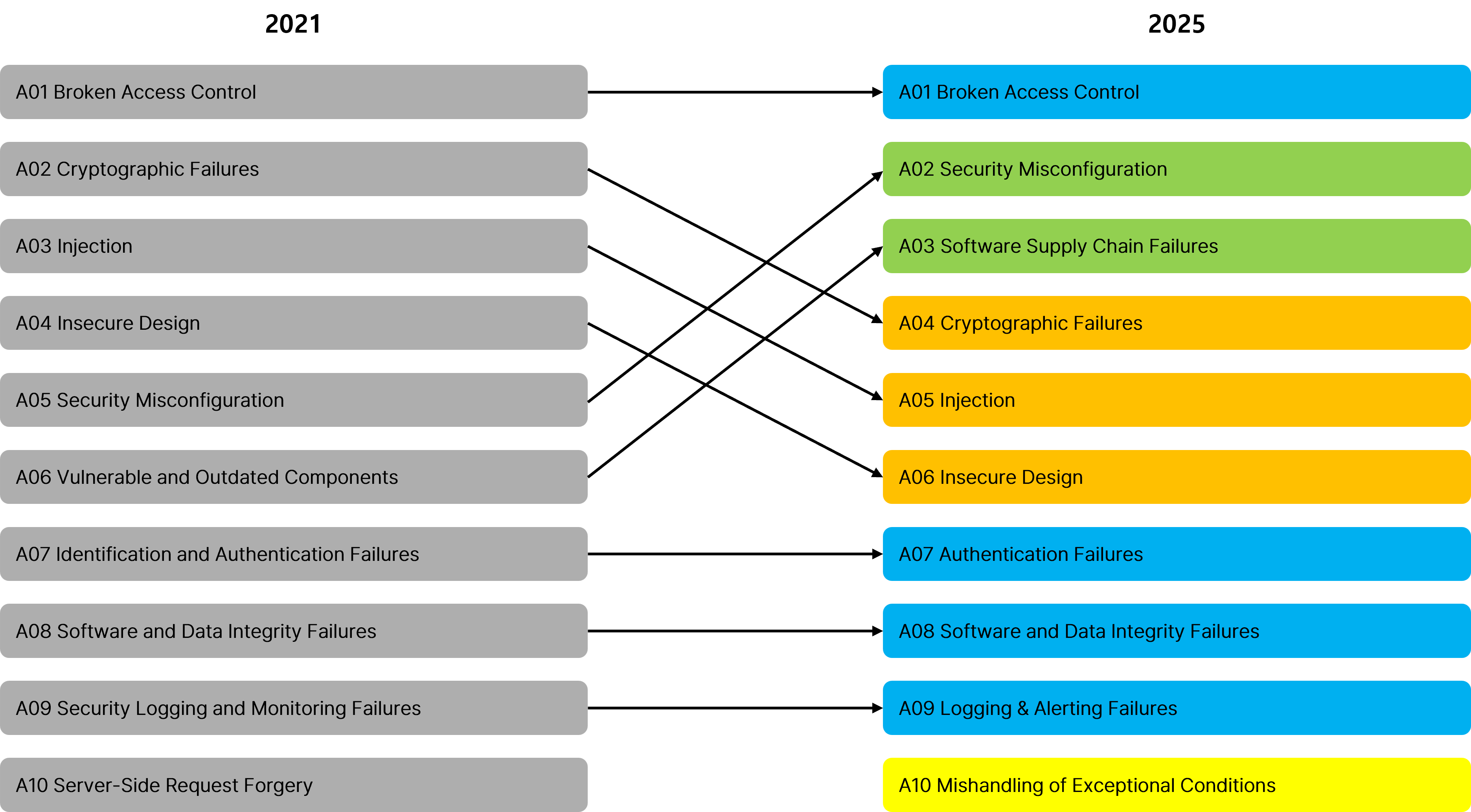
| Code | Name | Key Changes |
| A01:2025 | Broken Access Control | Remains the top threat, highlighting persistent challenges in access restrictions. |
| A02:2025 | Security Misconfiguration | Jumps from 5th to 2nd place due to increasingly complex and customizable deployment environments. Found in 3.00% of tested apps. |
| A03:2025 | Software Supply Chain Failures | A major new category that expands on 2021’s “Vulnerable and Outdated Components” by addressing threats across dependencies, build systems, and deployment infrastructure. Though rare, these failures can cause severe damage and topped community concern surveys. |
| A04:2025 | Cryptographic Failures | Drops from 2nd to 4th but remains critical due to risks of sensitive data exposure and system breaches. |
| A05:2025 | Injection | Drops two places, still includes risks like XSS and SQL Injection. |
| A06:2025 | Insecure Design | Declines from 4th to 6th. Introduced in 2021, this category reflects improvements in threat modeling and secure design practices. |
| A07:2025 | Authentication Failures | Holds steady in 7th place with slight name refinement. The rise in standardized authentication frameworks has helped reduce vulnerabilities. |
| A08:2025 | Software or Data Integrity Failures | Stays at 8th place, focusing on trust boundary failures and lack of integrity checks for code, software, and data artifacts. |
| A09:2025 | Logging & Alerting Failures | Also remains at 9th with an updated name. Now emphasizes the importance of alerting, not just logging. Often underestimated in data but ranked high by community votes. |
| A10:2025 | Mishandling of Exceptional Conditions | The only new addition. Covers 24 CWEs related to poor error handling, logic flaws, and data leaks under abnormal conditions. |
How to Protect Against OWASP Top 10 Threats
The OWASP Top 10:2025 RC1 clearly signals a shift in web security—from simply defending against external attacks to emphasizing secure design and trust verification within the application itself.
Rather than wait for the final release, organizations should act now. Use the RC1 insights—especially around design (A06), configuration (A02), and supply chain (A03)—to reevaluate your security strategies and development workflows.
Cybersecurity is no longer optional. It is a competitive advantage. Web Application Firewalls (WAF/WAAP) and encryption platforms are essential front-line defenses, forming the foundation of a strong defense-in-depth strategy.
Click here to subscribe our Newsletter
Click here for inquiries regarding the partner system of Penta Security
Check out Penta Security’s product lines:
Web Application Firewall: WAPPLES
Database Encryption: D.AMO
Check out the product lines of Cloudbric by Penta Security:
Cloud-based Fully Managed WAAP: Cloudbric WAF+
Agent based Zero Trust Network Access Solution: Cloudbric PAS
Agentless Zero Trust Network Access Solution: Cloudbric RAS
Click here for inquiries regarding the partner system of Cloudbric